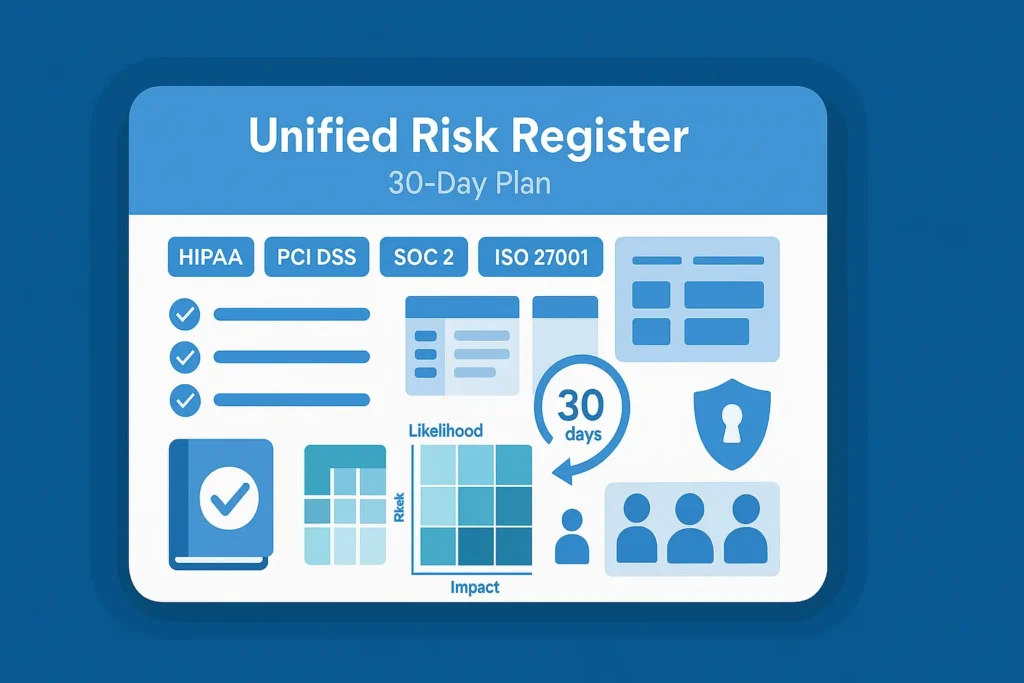
7 Proven Steps to a Unified Risk Register (30 Days)
If you juggle HIPAA, PCI DSS, SOC 2, ISO 27001 and GDPR, you don’t need five plans—you need one Unified Risk Register and a 30-day, evidence-first remediation sprint auditors will accept. This guide shows exactly how to scope, analyze gaps, score risk, generate a prioritized backlog, assign RACI, and package an audit-ready evidence binder—plus copy-paste code to automate as much as possible.
For a practical checklist, see our new guide on SOC 2 Type II evidence artifacts.
Quick jump links:
- Services: Risk Assessment Services, Remediation Services (map and fix fast).
What “Unified Risk Register” means (and why it wins)
A Unified Risk Register consolidates overlapping requirements across frameworks into a single record per risk, with fields for source framework(s), mapped controls, inherent/residual scoring, treatment, owner, due date, and evidence pointers. You’ll execute one sprint and hand auditors one well-indexed evidence pack instead of five parallel efforts.
The 30-Day Plan at a Glance
- Week 1: Scope & data collection
- Week 2: Gap analysis & control mapping
- Week 3: Risk scoring, prioritized backlog, RACI
- Week 4: Remediation sprint & evidence binder handoff
Along the way, leverage our Risk Assessment Services to accelerate discovery and our Remediation Services to close gaps with auditor-ready proof.
Free Website Vulnerability Scanner hero (screenshot):

Step 1 — Scope (systems, data, and “in scope” regs)
Deliverables: system inventory, data flows, scope statement, acceptance by stakeholders.
Do this:
- Identify critical functions (PHI, cardholder data, TSC, Annex A domains, personal data processing).
- Inventory apps/APIs, cloud accounts, endpoints, identity providers, third parties.
- Mark assurance boundaries for HIPAA/PCI/SOC 2/ISO/GDPR.
Automation (CSV template for import):
system_id,name,owner,data_classes,frameworks,tags
pay-api,Payments API,Eng Lead,"PAN,PII",PCI DSS|SOC2,prod|internet_exposed
ehr,EMR App,CTO,"PHI,PII",HIPAA|SOC2,prod|restricted
idp,SSO/IdP,SRE Lead,"PII",SOC2|ISO27001,shared|authStep 2 — Gap analysis (map controls once, reuse everywhere)
Goal: One control map feeding all frameworks.
Control map schema (JSON):
{
"U-CTRL-0001": {
"name": "Encrypt data at rest (server-side keys)",
"frameworks": {
"HIPAA": ["164.312(a)(2)(iv)"],
"PCI_DSS": ["3.5", "3.6"],
"SOC2": ["CC6.1","CC6.7"],
"ISO27001": ["A.8.24","A.8.25"],
"GDPR": ["Art.32(1)(a)"]
}
},
"U-CTRL-0002": {
"name": "Log retention & tamper-evidence",
"frameworks": {
"SOC2": ["CC7.2","CC7.3"],
"ISO27001": ["A.8.15"],
"HIPAA": ["164.312(b)"],
"PCI_DSS": ["10.4","10.5"]
}
}
}Python: build the Unified Risk Register from raw findings
import csv, json, datetime
MAP = json.load(open("control_map.json"))
def map_to_unified(controls):
u = set()
for f_ctrl in controls: # e.g., ("PCI_DSS","3.5")
for uctrl, meta in MAP.items():
if f_ctrl[0] in meta["frameworks"] and f_ctrl[1] in meta["frameworks"][f_ctrl[0]]:
u.add(uctrl)
return sorted(u)
with open("raw_findings.csv") as f, open("unified_register.csv","w",newline="") as out:
r, w = csv.DictReader(f), csv.DictWriter(out, fieldnames=[
"risk_id","title","systems","unified_controls","framework_refs","status","owner","due","evidence_path"
])
w.writeheader()
for i,row in enumerate(r, start=1):
refs = [(row["framework"], c) for c in row["controls"].split("|")]
u_ctrls = map_to_unified(refs)
w.writerow({
"risk_id": f"R-{i:04d}",
"title": row["title"],
"systems": row["systems"],
"unified_controls": "|".join(u_ctrls),
"framework_refs": row["controls"],
"status": "Open",
"owner": "",
"due": (datetime.date.today()+datetime.timedelta(days=30)).isoformat(),
"evidence_path": ""
})Step 3 — Risk scoring (likelihood × impact + quick modifiers)
SQL: compute scores and tiers
-- risks(risk_id,likelihood,impact,detectability_mod,compensating_mod)
-- Likelihood/Impact: 1..5 ; Mods: negative numbers reduce risk
SELECT
risk_id,
likelihood,
impact,
detectability_mod,
compensating_mod,
(likelihood * impact) + detectability_mod + compensating_mod AS score,
CASE
WHEN (likelihood * impact) >= 15 THEN 'High'
WHEN (likelihood * impact) BETWEEN 8 AND 14 THEN 'Medium'
ELSE 'Low'
END AS tier
FROM risks
ORDER BY score DESC;Heat calculation in Python (for dashboards):
import pandas as pd
df = pd.read_csv("unified_register.csv")
df["likelihood"]=df["likelihood"].astype(int)
df["impact"]=df["impact"].astype(int)
df["score"]=df["likelihood"]*df["impact"]
df["tier"]=pd.cut(df["score"], bins=[-1,7,14,25], labels=["Low","Medium","High"])
df.to_csv("unified_scored.csv", index=False)Step 4 — Prioritized backlog (turn risks into fix-tasks)
Backlog rule of thumb: Fix High in ≤14 days, Medium in ≤30 days, Low in next cycle. Group by unified control to avoid duplicate effort.
Jira JQL:
project = SEC AND labels in (UnifiedRiskRegister)
ORDER BY priority DESC, duedate ASCGitHub Issues (automation via CLI):
while IFS=, read -r risk_id title tier owner due; do
gh issue create --title "$risk_id: $title" \
--label UnifiedRiskRegister,"Tier:$tier" \
--assignee "$owner" \
--project "Security Remediation" \
--milestone "30-Day Unified Sprint" \
--body "Due: $due"
done < backlog.csvStep 5 — RACI (clarity kills delays)
| Task | R | A | C | I |
|---|---|---|---|---|
| Validate scope & data flows | SecEng | CISO | AppOwners | Compliance |
| Approve risk criteria & thresholds | CISO | CEO | Compliance | Legal |
| Implement encryption at rest | Cloud | SRE | AppOwners | Compliance |
| Log retention policy & controls | SecEng | CISO | IT Ops | Auditors |
| Evidence binder assembly | Compliance | CISO | SecEng | Auditors |
Tip: keep owners stable across frameworks (same people, one sprint).
Step 6 — Evidence binder (auditor-ready, one index)
Folder recipe:
/evidence/
00-index.md
10-scope/
20-gaps-map/
30-risk-scores/
40-remediation/
50-policies/
60-change-tickets/
70-screenshots/
80-logs/Python: assemble an index automatically
import os, hashlib, time
root="evidence"
with open(os.path.join(root,"00-index.md"),"w") as idx:
idx.write("# Evidence Index\n\n")
for base, _, files in os.walk(root):
for f in files:
if f.endswith((".pdf",".png",".csv",".txt",".md",".json",".yaml")):
p = os.path.join(base,f)
h = hashlib.sha256(open(p,"rb").read()).hexdigest()[:12]
idx.write(f"- {p} \n - sha256: `{h}` \n - mtime: {time.ctime(os.path.getmtime(p))}\n")GitHub Actions: nightly artifact
name: Evidence Binder
on:
schedule: [{cron: "0 1 * * *"}]
workflow_dispatch:
jobs:
pack:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- run: python tools/build_evidence_index.py
- run: tar -czf evidence-$(date +%F).tgz evidence
- uses: actions/upload-artifact@v4
with: {name: evidence, path: evidence-*.tgz}Step 7 — Sprint execution (fixes that move all frameworks)
Focus on controls with the widest cross-framework payoff.
Policy-as-code (OPA/Rego) examples:
Require S3 encryption & no public buckets:
package cloud.s3
deny[msg] {
input.bucket.public == true
msg := sprintf("Bucket %s is public", [input.bucket.name])
}
deny[msg] {
not input.bucket.encryption.kms_key_id
msg := sprintf("Bucket %s missing KMS encryption", [input.bucket.name])
}Cloud evidence (AWS CLI):
aws s3api get-bucket-encryption --bucket prod-logs | tee evidence/70-screenshots/s3_encryption.json
aws s3api get-bucket-policy-status --bucket prod-logs | tee evidence/70-screenshots/s3_policy_status.json
aws iam get-account-password-policy | tee evidence/80-logs/iam_pw_policy.json
aws cloudtrail describe-trails | tee evidence/80-logs/cloudtrail.jsonWindows evidence (PowerShell):
wevtutil qe Security /q:"*[System[(EventID=1102)]]" /c:5 /f:text > evidence\80-logs\audit_clears.txt
Get-LocalGroupMember -Group "Administrators" | Out-File evidence\80-logs\local_admins.txt
Get-MpComputerStatus | ConvertTo-Json | Out-File evidence\80-logs\defender_status.jsonAppSec quick wins (HTTP headers):
add_header Content-Security-Policy "default-src 'self'";
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
add_header X-Frame-Options "DENY";
add_header X-Content-Type-Options "nosniff";How it all ties to each framework (examples)
- HIPAA: audit controls, integrity, transmission security → logging, encryption, access controls.
- PCI DSS: cardholder data encryption, logging, vulnerability mgmt → S3/KMS, CloudTrail, WAF rules, patch cadence.
- SOC 2: CC6/7/8 coverage through access control, monitoring, change management.
- ISO 27001: Annex A mappings for cryptography, logging, supplier mgmt.
- GDPR: Article 32 security, DPIAs, records of processing, retention controls.
One unified fix often reduces risk across all five.
Sample report to check Website Vulnerability (from the scanner):

(For deeper discovery and mapping help, book our Risk Assessment Services and move straight into the sprint with a clean backlog.)
Recent related reading
- Android Security Bulletin November 2025: 72-Hour Playbook (good example of evidence-driven rollout).
- NIST CSF 2.0: 14-Day Exclusive Plan for Board-Ready Metrics (metrics you can reuse in your evidence binder).
- 7 Proven Steps for CMMC Level 2 Remediation (another unified sprint pattern).
- DORA TLPT 2025: 7 Powerful Moves to Fix First (governance and threat-led insights).
Browse all posts on our Cybersecurity Blog.
Implementation starter pack (copy/paste)
Unified Risk Register item (YAML):
risk_id: R-0027
title: Missing S3 encryption at rest for prod-logs
systems: s3:prod-logs
unified_controls: [U-CTRL-0001]
framework_refs:
HIPAA: ["164.312(a)(2)(iv)"]
PCI_DSS: ["3.5","3.6"]
SOC2: ["CC6.7"]
ISO27001: ["A.8.24"]
GDPR: ["Art.32(1)(a)"]
likelihood: 4
impact: 4
tier: High
owner: Cloud
due: 2025-12-09
treatment: Implement SSE-KMS; block public access; enforce bucket policy
evidence:
- evidence/70-screenshots/s3_encryption.json
- evidence/80-logs/cloudtrail.json
status: OpenBacklog exporter (CSV → Jira):
# inputs: unified_scored.csv; outputs: backlog.csv (risk_id,title,tier,owner,due)
import csv
rows=[]
with open("unified_scored.csv") as f:
for r in csv.DictReader(f):
if r["tier"] in ("High","Medium"):
rows.append([r["risk_id"], r["title"], r["tier"], r["owner"] or "seceng", r["due"]])
with open("backlog.csv","w",newline="") as o:
csv.writer(o).writerows(rows)Conftest (OPA) run for IaC folders:
conftest test terraform/ kubernetes/ -o table | tee evidence/80-logs/policy_as_code.txtWhen to ask for help (and get there faster)
- Need a clean scope, gap map, and prioritized backlog this week? Our Risk Assessment Services kickstart your Unified Risk Register with audit-ready artifacts.
- Want engineers to implement and package the evidence binder? Our Remediation Services deliver fixes and proof aligned to each framework.
You can also take a quick baseline with the Free Website Vulnerability Scanner to feed early wins into your register: free.pentesttesting.com.
This article is designed for compliance & risk leaders who want one register, one sprint, and one evidence pack—without sacrificing rigour.
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about Unified Risk Register in 30 Days.

