
ISO 27001 Remediation Services
Risk assessments uncover issues. Our job is to fix them.
From policy rewrites and control implementation to evidence collection, we turn findings into certification-ready outcomes—your complete ISO 27001 implementation support.
⚠️ Why Remediation is Critical
A risk assessment without remediation is a diagnosis without treatment. Ignored findings lead to:
- Nonconformities (majors/minors) in Stage 1/Stage 2.
- Security incidents, downtime, and customer distrust.
- Contract delays and insurance issues.
Remediation proves control effectiveness and keeps your ISMS improving.
🛠️ What We Fix (Examples)
- Policies & Procedures – ISMS manual, SoA, access control, crypto, logging, supplier management, secure dev, backup/BCP/DR.
- Technical Controls – MFA, least privilege, log retention, EDR/AV, encryption at rest/in transit, patching, vulnerability mgmt.
- Risk Treatment Execution – Implement selected controls; justify residual risk.
- Evidence Collection – Screenshots, tickets, configs, training logs, vendor due-diligence.
- Internal Audit Follow-ups – Corrective actions (CAPA), root-cause analysis.
- Supplier/Vendor Risk – DPA/ISMS requirements, due-diligence questionnaires.
- Awareness & Training – Targeted refreshers to close human-factor gaps.
🚀 Our Remediation Process
1️⃣ Findings Review:
Gap list, risk register, nonconformities, and priorities
2️⃣ Remediation Plan & RACI:
Owners, due dates, acceptance criteria, success metrics
3️⃣ Implementation Sprints:
Policies & controls deployed with change management
4️⃣ Evidence & SoA Update:
Capture artifacts and update SoA/treatment status
5️⃣ Pre-Audit Validation:
Mock audit; resolve minors; package evidence for auditor
👥 Who Needs ISO 27001 Remediation Services?
- Teams aiming for first-time certification
- Certified orgs addressing surveillance findings
- Fast-growing startups adding new products/clouds
- Vendors needing ISO for enterprise deals
⭐ Why Choose Pentest Testing Corp.
- End-to-End Partner – From risk assessment to remediation to internal audit.
- Evidence-First – We don’t just fix; we prove fixes with audit-ready artifacts.
- Security Engineering – Changes that actually reduce risk, not just tick boxes.
- Proven Track Record – Trusted by SaaS, FinTech, HealthTech, and enterprises.
Explore more: Compliance & Risk Management Services • Testimonials • Contact Us
⭐ What Our Clients Say
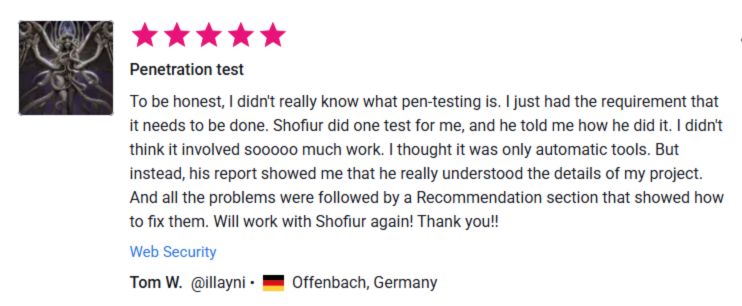

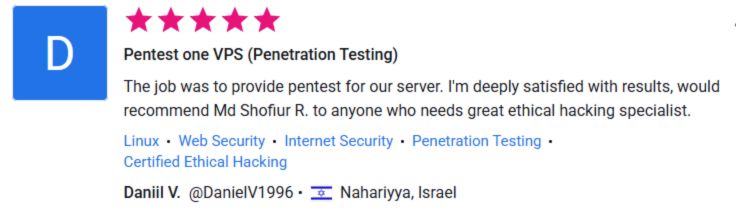
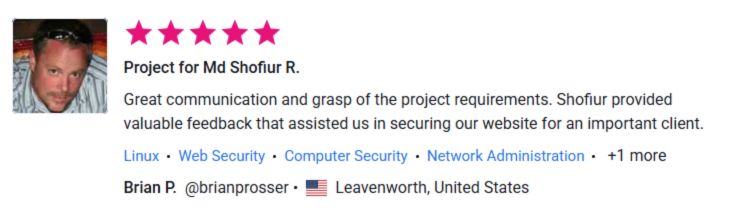
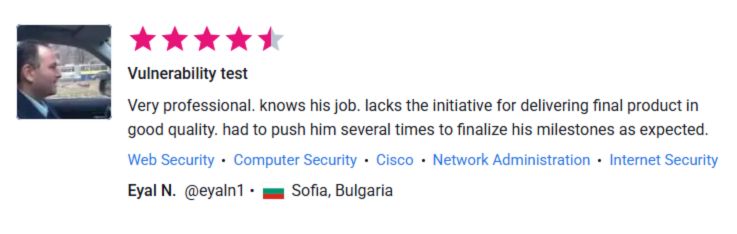
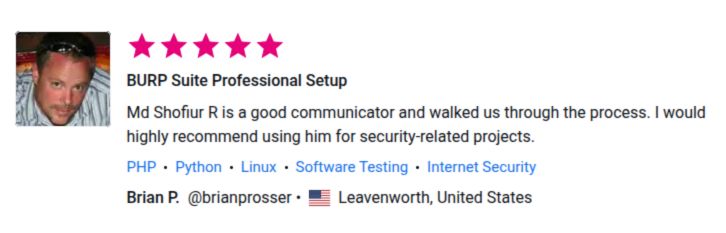
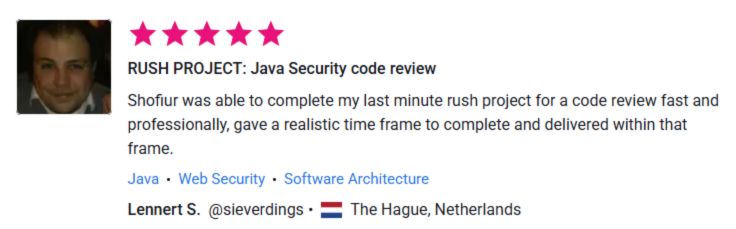
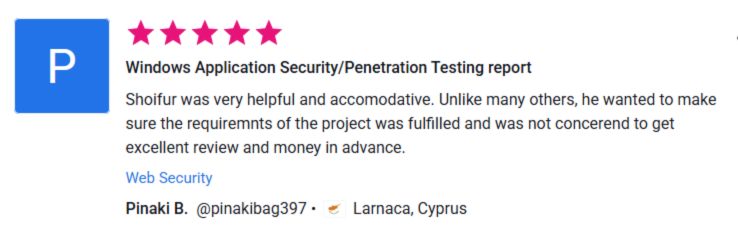
See More Client Results
Want to read more verified feedback and real-world outcomes from our engagements?
Explore our dedicated Testimonials page for detailed success stories across web, mobile, cloud, and AI app security.
Transparent Pricing:
Every business is unique. Contact us to get a customized quote based on your organization’s needs, infrastructure, and compliance requirements.
Recent Case Studies
From vulnerability assessments to full-scale pentests — see how we deliver measurable impact.
Would you like to resell or refer our services to your clients?
👉 Learn more about our Cybersecurity Agency Partnership Program
https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about our products and services.
🚨 Need urgent investigation support?
If you’re seeing suspicious logins, malicious pop-ups, unknown apps, or ransomware activity, our Forensic Analysis Services can help you quickly validate compromise and secure your systems.
✅ Windows | macOS | Android | iOS | Email | Cloud ——— 👉 https://www.pentesttesting.com/digital-forensic-analysis-services/


