9 Powerful Fixes for Sensitive Data Exposure in WordPress
If you collect logins, emails, orders, or any personally identifiable information (PII), Sensitive Data Exposure is your highest-impact risk. Data leaks don’t always come from “hackers”—they often happen through misconfigurations, verbose error logs, unsafe backups, public buckets, insecure cookies, or plugins exposing the REST API. In this guide, you’ll lock down Sensitive Data Exposure in WordPress step-by-step with practical snippets, server rules, and developer patterns you can ship today.

We’ve included many coding examples (Apache/Nginx, PHP, WP-CLI, and more) so your team can quickly harden WordPress, reduce data leakage, and meet common compliance expectations (GDPR/PCI). You’ll also find internal links to related tutorials and service pages to keep your security posture strong across your stack.
What does “sensitive data” mean for WordPress?
- PII: names, emails, phone numbers, addresses
- Authentication secrets: passwords, reset tokens, API keys, JWTs
- Financial data: order details, payment references (never store raw card data)
- Health/other regulated data (if applicable)
- Session identifiers and cookies
When any of the above is mishandled (debug pages, public logs, exposed backups, misconfigured file storage/CDN), you get Sensitive Data Exposure Issues—often without noticing for weeks.
Quick win checklist
- Force HTTPS and add HSTS
- Turn off debug display and redact errors
- Lock down
wp-config.php, salts, and secrets - Set
Secure,HttpOnly, andSameSiteon cookies - Deny access to backups, logs, and raw uploads with server rules
- Add security headers (CSP, Referrer-Policy, X-Content-Type-Options)
- Restrict REST API exposure for non-authenticated users
- Encrypt sensitive custom fields at rest
- Use private object storage and signed URLs for downloads
- Scan regularly for Website Security checks and monitor for new exposures
1) Force HTTPS & HSTS (eliminate plaintext leaks)
Apache (.htaccess):
# Redirect all HTTP to HTTPS
RewriteEngine On
RewriteCond %{HTTPS} !=on
RewriteRule ^ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L]
# HSTS: tell browsers to only use HTTPS
<IfModule mod_headers.c>
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload"
</IfModule>Nginx:
server {
listen 80;
server_name example.com www.example.com;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl http2;
server_name example.com www.example.com;
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload" always;
# ssl_certificate /path/fullchain.pem; ssl_certificate_key /path/privkey.pem;
}2) Turn off debug display & mask errors (no sensitive stack traces)
wp-config.php:
define('WP_DEBUG', false);
define('WP_DEBUG_DISPLAY', false);
@ini_set('display_errors', 0);Centralized error redaction (wp-content/mu-plugins/redact-errors.php):
<?php
/**
* Plugin Name: Redact Error Output
*/
if (!defined('ABSPATH')) exit;
set_error_handler(function($errno, $errstr, $errfile, $errline) {
// Never echo raw errors; log a minimal message
error_log("[WP] Error at $errfile:$errline");
return true; // handled
});This prevents accidental Sensitive Data Exposure in WordPress via notices/warnings that reveal paths, SQL fragments, or secrets.
3) Harden wp-config.php, keys, and secrets
wp-config.php (baseline hardening):
define('DISALLOW_FILE_EDIT', true);
define('AUTOSAVE_INTERVAL', 300);
define('WP_POST_REVISIONS', 10);
// Load salts/keys from environment (never hardcode in repo)
define('AUTH_KEY', getenv('AUTH_KEY'));
define('SECURE_AUTH_KEY', getenv('SECURE_AUTH_KEY'));
define('LOGGED_IN_KEY', getenv('LOGGED_IN_KEY'));
define('NONCE_KEY', getenv('NONCE_KEY'));
define('AUTH_SALT', getenv('AUTH_SALT'));
define('SECURE_AUTH_SALT',getenv('SECURE_AUTH_SALT'));
define('LOGGED_IN_SALT', getenv('LOGGED_IN_SALT'));
define('NONCE_SALT', getenv('NONCE_SALT'));Deny direct access at the web server:
Apache:
<Files wp-config.php>
Require all denied
</Files>
# Also deny .env or other dotfiles
<FilesMatch "^\.">
Require all denied
</FilesMatch>Nginx:
location ~* wp-config.php { deny all; }
location ~ /\. { deny all; }Keeping secrets out of the repo and inaccessible via the web reduces Sensitive Data Exposure from misconfigured servers or leaked backups.
4) Set secure cookie flags (protect sessions)
Apache (.htaccess):
<IfModule mod_headers.c>
Header always edit Set-Cookie "(?i)^((?:(?!;).)*)" "$1; HttpOnly; Secure; SameSite=Strict"
</IfModule>Nginx:
proxy_cookie_path / "/; HttpOnly; Secure; SameSite=Strict";WordPress hook (mu-plugin) to hard-set flags:
<?php
/**
* Plugin Name: Secure Cookies
*/
add_filter('secure_auth_cookie', '__return_true');
add_filter('logged_in_cookie', function($cookie){
// WordPress core sets flags, but ensure strictness:
@ini_set('session.cookie_httponly', 1);
@ini_set('session.cookie_secure', 1);
return $cookie;
});5) Deny access to backups, logs, and raw uploads
Apache (.htaccess):
# Block common backup/log file types
<FilesMatch "\.(sql|zip|gz|bak|old|log)$">
Require all denied
</FilesMatch>
# Prevent directory listing everywhere
Options -IndexesNginx:
location ~* \.(sql|zip|gz|bak|old|log)$ { deny all; }
autoindex off;Tip: Don’t rely on robots.txt to hide sensitive content—it’s a hint for crawlers, not a security control.
6) Add modern security headers (limit data exfil paths)
Apache (.htaccess):
<IfModule mod_headers.c>
Header always set X-Content-Type-Options "nosniff"
Header always set Referrer-Policy "strict-origin-when-cross-origin"
Header always set X-Frame-Options "SAMEORIGIN"
Header always set Permissions-Policy "geolocation=(), microphone=(), camera=()"
Header always set Content-Security-Policy "default-src 'self'; img-src 'self' data: https:; script-src 'self' 'unsafe-inline' 'unsafe-eval' https:; style-src 'self' 'unsafe-inline' https:; frame-ancestors 'self'; base-uri 'self'"
</IfModule>Nginx:
add_header X-Content-Type-Options "nosniff" always;
add_header Referrer-Policy "strict-origin-when-cross-origin" always;
add_header X-Frame-Options "SAMEORIGIN" always;
add_header Permissions-Policy "geolocation=(), microphone=(), camera=()" always;
add_header Content-Security-Policy "default-src 'self'; img-src 'self' data: https:; script-src 'self' 'unsafe-inline' 'unsafe-eval' https:; style-src 'self' 'unsafe-inline' https:; frame-ancestors 'self'; base-uri 'self'" always;CSP reduces the blast radius of XSS and widget sprawl that can silently leak PII—another common cause of Sensitive Data Exposure.
7) Restrict what the REST API exposes publicly
Block unauthenticated access to sensitive endpoints:
<?php
/**
* Plugin Name: REST Guard
*/
add_filter('rest_authentication_errors', function($result){
if(!is_user_logged_in()){
// Allow basic health endpoints, block user/content metadata by default
$allowed = [
'/wp/v2/statuses',
'/wp/v2/types',
];
$req = $_SERVER['REQUEST_URI'] ?? '';
foreach ($allowed as $ok) {
if (strpos($req, $ok) !== false) return $result;
}
return new WP_Error('rest_forbidden', 'Authentication required', ['status'=>401]);
}
return $result;
});Selective field filtering (avoid PII fields):
add_filter('rest_prepare_user', function($response) {
if(!$response || !is_array($response->data)) return $response;
unset($response->data['email']); // hide email
unset($response->data['first_name']);
unset($response->data['last_name']);
return $response;
}, 10, 3);This prevents Sensitive Data Exposure in WordPress through publicly consumable JSON.
8) Encrypt sensitive custom fields at rest (sodium)
If you store PII in custom user meta or post meta, encrypt it before writing.
Encrypt/decrypt helpers (mu-plugin):
<?php
/**
* Plugin Name: Meta Encryptor
*/
if (!defined('ABSPATH')) exit;
function mcrypt_key(): string {
$k = getenv('WP_SODIUM_KEY');
if (!$k) { error_log('Missing WP_SODIUM_KEY'); }
return $k ?: str_repeat('0', 32);
}
function encrypt_meta($plaintext) {
$key = mcrypt_key();
$nonce = random_bytes(SODIUM_CRYPTO_SECRETBOX_NONCEBYTES);
$cipher = sodium_crypto_secretbox($plaintext, $nonce, $key);
return base64_encode($nonce.$cipher);
}
function decrypt_meta($encoded) {
$key = mcrypt_key();
$data = base64_decode($encoded, true);
if (!$data) return false;
$nonce = substr($data, 0, SODIUM_CRYPTO_SECRETBOX_NONCEBYTES);
$cipher = substr($data, SODIUM_CRYPTO_SECRETBOX_NONCEBYTES);
return sodium_crypto_secretbox_open($cipher, $nonce, $key);
}
// Usage example:
update_user_meta($user_id, 'pii_phone', encrypt_meta('+1-555-0100'));
// get: decrypt_meta(get_user_meta($user_id, 'pii_phone', true));By encrypting at rest, a database snapshot or stolen SQL dump is less likely to cause Sensitive Data Exposure.
9) Private object storage with signed URLs (no public buckets)
Keep invoices, exports, or PII-heavy downloads in private storage and serve temporary links.
PHP (AWS S3 pre-signed URL concept):
<?php
// Install AWS SDK via composer in a safe location, then:
use Aws\S3\S3Client;
$s3 = new S3Client([
'version' => 'latest',
'region' => 'us-east-1',
'credentials' => [
'key' => getenv('AWS_ACCESS_KEY_ID'),
'secret' => getenv('AWS_SECRET_ACCESS_KEY')
]
]);
$cmd = $s3->getCommand('GetObject', [
'Bucket' => 'my-private-bucket',
'Key' => 'reports/user-1234.pdf'
]);
$request = $s3->createPresignedRequest($cmd, '+10 minutes');
$presignedUrl = (string) $request->getUri();
// echo link to $presignedUrl only for authorized usersThis pattern avoids direct public exposure of sensitive files and helps eliminate Sensitive Data Exposure caused by mis-shared assets.
Extra hardening patterns (copy-paste friendly)
Block upload execution (Apache in /wp-content/uploads):
<FilesMatch "\.(php|phar|phtml)$">
Require all denied
</FilesMatch>Nginx equivalent:
location ~* /wp-content/uploads/.*\.(php|phar|phtml)$ { deny all; }Sanitize request bodies and strip secrets from logs (PHP front controller):
// mu-plugins/redact-logs.php
add_filter('http_request_args', function($args, $url){
if (!empty($args['body'])) {
$args['body'] = preg_replace('/("password"\s*:\s*")[^"]+"/i', '$1***"', $args['body']);
$args['body'] = preg_replace('/("token"\s*:\s*")[^"]+"/i', '$1***"', $args['body']);
}
return $args;
}, 10, 2);WP-CLI: purge revision bloat (reduces leakage via backups):
wp post list --post_type=post --format=ids | xargs -I % wp post delete % --force
wp transient delete --allMySQL minimal grants for app user (principle of least privilege):
CREATE USER 'wpapp'@'%' IDENTIFIED BY 'use-strong-pass-here';
GRANT SELECT, INSERT, UPDATE, DELETE, CREATE, INDEX, ALTER ON wp_production.* TO 'wpapp'@'%';
FLUSH PRIVILEGES;Server-level rate limiting to protect the login and REST endpoints (Nginx):
limit_req_zone $binary_remote_addr zone=one:10m rate=10r/s;
location /wp-login.php {
limit_req zone=one burst=20 nodelay;
}
location ~* /wp-json/ {
limit_req zone=one burst=40 nodelay;
}Test & monitor (catch silent exposures)
Run a fast external scan after each deployment or plugin update to catch misconfigurations.
👉 Try our free Website Vulnerability Scanner to spot exposed files, headers, and known CVEs: https://free.pentesttesting.com/
Screenshot of the Website Vulnerability Scanner tool homepage

After fixing issues, rescan to validate your hardening. Keep doing this routinely (e.g., weekly) and after major changes.
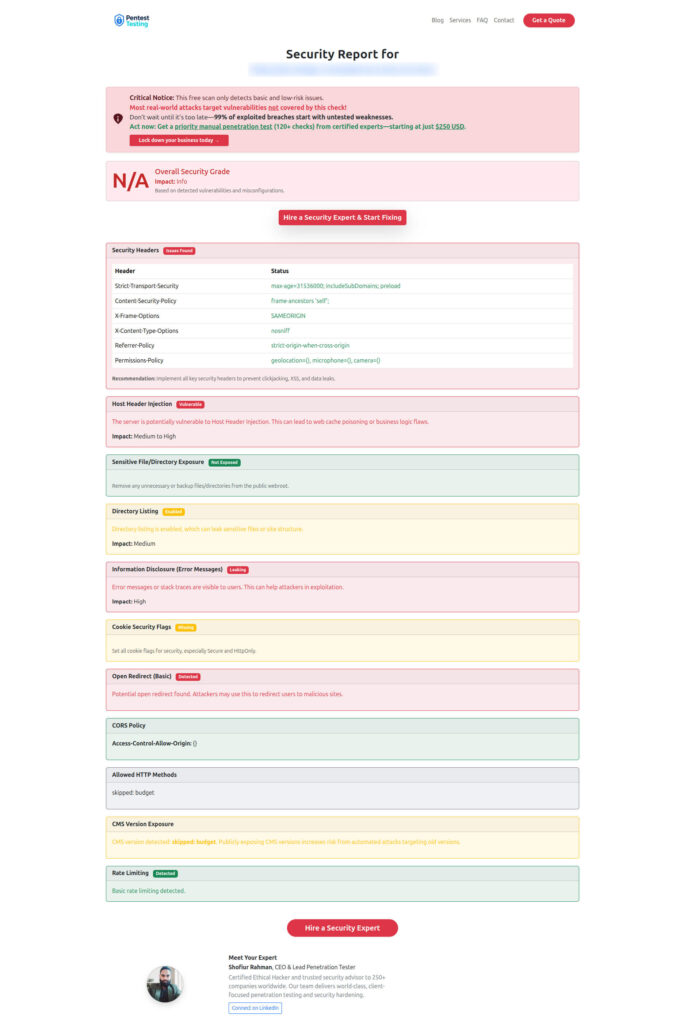
Sample Assessment Report by our free tool to check Website Vulnerability
Related, in-depth tutorials (keep learning)
- Tackling XML injection patterns (front-end example):
https://www.cybersrely.com/prevent-xml-injection-in-react-js/ - Lock down auth flows to avoid chained exposures:
https://www.pentesttesting.com/broken-authentication-in-wordpress/ - Backend payload hardening for XML in Laravel:
https://www.pentesttesting.com/prevent-xml-injection-in-laravel-securely/ - Security Misconfiguration in WordPress:
https://www.pentesttesting.com/security-misconfiguration-in-wordpress/ - Big-picture context on threat trends:
https://www.pentesttesting.com/top-7-cybersecurity-threats/
Each of these helps prevent mistakes that often lead to Sensitive Data Exposure via chained bugs.
Service add-ons that close the gaps
Managed IT Services (proactive, 24/7)
From patch cycles to backup policy, our Managed IT Services reduce the operational risks that create Sensitive Data Exposure in WordPress. We’ll enforce encryption, access controls, and secure storage end-to-end.
➡️ https://www.pentesttesting.com/managed-it-services/
AI Application Cybersecurity (modern apps, safer data)
Using LLMs or AI features in your product? We secure prompts, datasets, and model outputs to ensure Sensitive Data Exposure in WordPress doesn’t happen through AI-powered workflows.
➡️ https://www.pentesttesting.com/ai-application-cybersecurity/
Offer Cybersecurity Service to Your Client (White-Label)
Agencies: package these hardening steps under your brand. We’ll do the heavy lifting while you deliver value—and prevent Sensitive Data Exposure for your clients at scale.
➡️ https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
End-to-end example: safe customer portal download flow
- User authenticates ➜ app verifies capability (role/capability check).
- App generates a signed URL for a private object (expires in 10 minutes).
- Response includes no PII in URL/query; headers instruct no-cache.
- Browser downloads via HTTPS; headers and CSP prevent data exfil.
WordPress controller sketch:
add_action('template_redirect', function(){
if (!is_user_logged_in() || !current_user_can('read_private_pages')) {
wp_die('Unauthorized', 401);
}
if (isset($_GET['download']) && $_GET['download'] === 'invoice') {
// Verify nonce to prevent CSRF
if (!wp_verify_nonce($_GET['_wpnonce'] ?? '', 'download-invoice')) {
wp_die('Invalid request', 400);
}
$url = my_generate_presigned_s3('invoices/'.get_current_user_id().'/latest.pdf', '+5 minutes');
nocache_headers(); // prevent caching of sensitive responses
wp_redirect($url);
exit;
}
});This pattern drastically limits opportunities for Sensitive Data Exposure.
Final thoughts
Security isn’t a one-time patch—it’s a lifecycle. By enforcing HTTPS, taming errors, locking down secrets, restricting the REST API, encrypting at rest, and serving private files via signed URLs, you’ll drastically reduce the risk of Sensitive Data Exposure in WordPress. Pair these steps with monitoring and routine scans using our free Website Security Scanner tool to stay ahead of regressions.
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about Sensitive Data Exposure in WordPress.

