
🕵️ Forensic Analysis Services (Digital Forensics & Incident Response)
⚠️ Has your PC been hacked?
📱 Is your Android or iPhone acting strange?
Seeing 🚫 malicious pop-ups, 🔁 weird redirects, 👤 unknown logins, 📩 messages sent from your account, or 💳 suspicious transactions?
Pentest Testing Corp provides professional Forensic Analysis (Digital Forensics / DFIR) to confirm what happened, preserve evidence, identify the attacker’s path, and give you clear next steps to recover—without guesswork.
✅ Windows | ✅ macOS | ✅ Android | ✅ iOS (iPhone/iPad) | ✅ Email | ✅ Cloud Accounts | ✅ Home & Business Devices
🌍 Trusted Security Partner (Worldwide)
We support consumers, startups, and enterprises globally—with practical investigation workflows designed to produce evidence-backed answers and actionable recovery steps.
🚨 Signs Your Device or Account May Be Compromised
If you notice one or more of these, it’s time to investigate:
- 🧨 Constant pop-ups / “virus alerts” / fake warnings
- 🌐 Browser redirects to strange sites or random extensions installed
- 📲 Unknown apps you didn’t install (or apps you can’t remove)
- 🔥 Battery draining fast / overheating / high data usage
- 🔑 Password changed / recovery email changed / MFA disabled
- 🕵️ New logins you don’t recognize (Google, Apple ID, Microsoft, Facebook, etc.)
- 📩 Your contacts receive spam messages “from you”
- 💳 Unauthorized banking/e-wallet activity
- 🔒 Files encrypted / ransom note / “pay to recover files”
- 🎥 Mic/camera indicators showing at unusual times
- 🛡️ Antivirus disabled or security settings changed unexpectedly
✅ We verify whether it’s malware/spyware, account takeover, phishing fallout, unsafe apps/extensions, or misconfiguration—then guide you safely.
📝 Note: Some mobile investigations depend on device state, backups, logs, and OS security restrictions. Even when deep extraction isn’t feasible, we still deliver high-confidence findings using available artifacts + account telemetry + correlation.
🎯 Why Forensic Analysis is Essential
Without proper forensics, people often:
- ❌ Remove the wrong thing (attacker remains)
- 🔁 Miss the entry point (reinfection happens)
- 📉 Underestimate impact (legal/compliance/insurance risk)
- 🧾 Lose evidence (weaker dispute/audit outcomes)
A proper forensic investigation delivers:
- 🧠 Root cause (how it started)
- 🧭 Timeline (what happened and when)
- 🎯 Impact (what was accessed/changed)
- 🛠️ Recovery plan (exact steps to secure everything)
🧪 Our Forensic Investigation Process (Simple & Structured)
1️⃣ Confidential Intake & Scoping
We collect symptoms, affected devices/accounts, timeframe, and goals.
2️⃣ Evidence Preservation (Safe & Controlled)
We guide what NOT to do (so evidence isn’t lost) and capture relevant data safely.
3️⃣ Analysis & Timeline Reconstruction
We correlate device activity, identity logs, email signals, and network indicators.
4️⃣ Root Cause & Attack Path
We identify the likely entry point: phishing, stolen credentials, OAuth abuse, malicious apps/extensions, unsafe downloads, or misconfiguration.
5️⃣ Impact Assessment & Containment
We confirm compromised accounts/devices and provide prioritized containment steps.
6️⃣ Final Report + Recovery Checklist
You get a clear report + step-by-step recovery checklist and prevention roadmap.
📦 What You’ll Receive (Deliverables)
- ✅ Hacked or not: clear conclusion with supporting evidence
- 🧩 Root cause analysis (how it happened)
- 🕒 Timeline of events (what occurred and when)
- 📌 Compromise scope (affected devices/accounts)
- 🔎 Indicators of compromise (IOCs) (apps/domains/IPs/hashes when applicable)
- 🧰 Recovery checklist (secure steps + prevention)
- 📁 Optional: Evidence handling records (hash verification / formal documentation)
🧠 Common Hacking Scenarios We Handle
- 📱 “My Facebook/Instagram/WhatsApp got hacked and email/phone changed”
- ✉️ “My Gmail/Outlook is sending messages I didn’t send”
- 🖥️ “My PC shows constant pop-ups and redirects”
- 🤖 “My Android has unknown apps and admin access”
- 🍎 “My iPhone shows Apple ID login alerts I didn’t trigger”
- ☁️ “Someone accessed my cloud files/storage”
- 🔒 “Ransomware encrypted my system”
- 👥 “Insider/ex-employee accessed company data”
⭐ What Our Clients Say
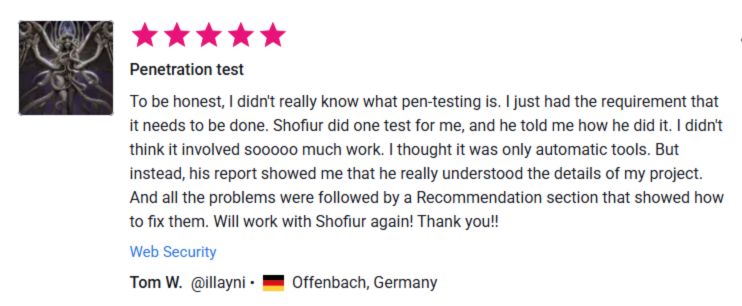

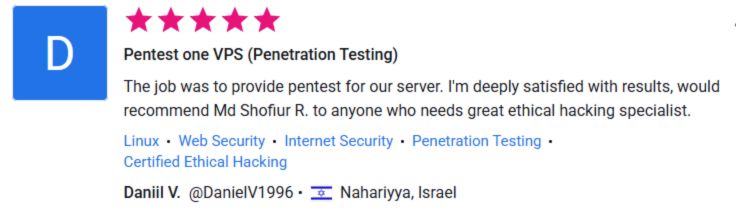
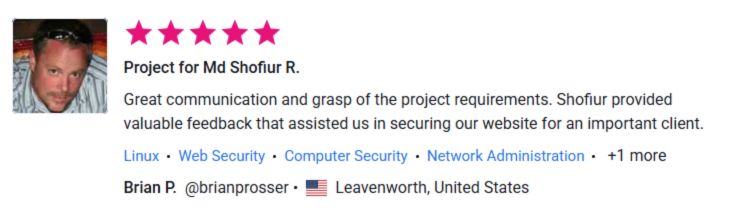
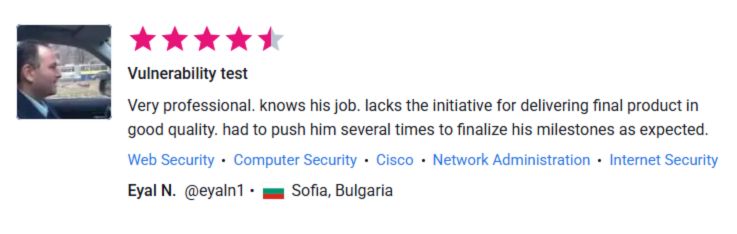
See More Client Results
Want to read more verified feedback and real-world outcomes from our engagements?
Explore our dedicated Testimonials page for detailed success stories across web, mobile, cloud, and AI app security.
Transparent Pricing:
Every business is unique. Contact us to get a customized quote based on your organization’s needs, infrastructure, and compliance requirements.
🏅 Why Choose Pentest Testing Corp
- 🧾 Evidence-first investigations (facts, timeline, impact)
- 🎯 Attacker-minded analysis (real-world tactics awareness)
- 🗣️ Clear communication (consumer-friendly + technical depth)
- 🔒 Confidential handling (privacy-focused approach)
- 🔁 End-to-end support: investigation → recovery → prevention
🛡️ Forensic Readiness (Prevent the Next Incident)
After investigation, strengthen prevention with:
- ✅ Risk Assessment Services: https://www.pentesttesting.com/risk-assessment-services/
- 🛠️ Remediation Services: https://www.pentesttesting.com/remediation-services/
- 🌐 Web App Penetration Testing: https://www.pentesttesting.com/web-app-penetration-testing-services/
- 🔌 API Pentest Testing: https://www.pentesttesting.com/api-pentest-testing-services/
- ☁️ Cloud Pentest Testing: https://www.pentesttesting.com/cloud-pentest-testing/
- 📱 Mobile App Pentest Testing: https://www.pentesttesting.com/mobile-application-pentest-testing/
Recent Case Studies
From vulnerability assessments to full-scale pentests — see how we deliver measurable impact.
Would you like to resell or refer our services to your clients?
👉 Learn more about our Cybersecurity Agency Partnership Program
https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about our products and services.
⚠️ Has your device been hacked or compromised? Don’t guess.
We investigate Windows, macOS, Android, iPhone/iOS, email, and cloud account compromises and deliver a clear, evidence-based recovery plan.
✅ Compliance & Risk Management Support
After a forensic investigation, many clients need help with audit readiness, control improvements, risk documentation, and compliance alignment. Our team can support you through our Compliance Risk Management Services: https://www.pentesttesting.com/compliance-risk-management-services/


