Broken Authentication in WordPress: 11 Proven Fixes
If you’re seeing suspicious logins, password-reset spam, or admin takeovers, you might be dealing with Broken Authentication in WordPress. This guide breaks down how attackers exploit login flows, sessions, and password resets—and then walks you through practical, copy-paste fixes. We’ll also show you where to test your site using a free scanner and link to deeper reads on related web-app security.

What is Broken Authentication in WordPress?
Broken Authentication describes flaws in login, session, and password-reset mechanisms that let attackers impersonate users or escalate to admin. Typical root causes include:
- Weak password policies or credential stuffing (reused passwords).
- No rate limiting on
/wp-login.phpandxmlrpc.php. - Insecure custom login code (bypassing core APIs).
- Predictable or persistent sessions (session fixation).
- Leaky user enumeration via REST API or errors.
- Insecure password reset workflows (CSRF/IDOR around tokens).
Symptoms and risk
- Random admin users appear or roles change mysteriously.
- “Password reset” emails flood your inbox.
- Logins from unfamiliar geographies or IP ranges.
- SEO spam pages suddenly publish under legitimate users.
Every one of these points may be a byproduct of Broken Authentication Vulnerability. The good news: most fixes are straightforward.
1) Always use core auth APIs (and avoid DIY password checks)
A classic mistake is verifying passwords directly against the database. Example of what not to do in a custom plugin:
// ❌ Insecure: bypasses WordPress auth APIs and can mishandle hashing
global $wpdb;
$user = $wpdb->get_row($wpdb->prepare("SELECT * FROM $wpdb->users WHERE user_login=%s", $_POST['user_login']));
if ($user && $_POST['user_pass'] === $user->user_pass) { // <- comparing raw password to hashed column!
wp_set_current_user($user->ID);
wp_set_auth_cookie($user->ID, true);
wp_redirect(admin_url());
exit;
}Use wp_signon() with sanitized inputs and nonces instead:
// ✅ Safer custom login handler using core APIs + nonce
function ptc_handle_login() {
if (!isset($_POST['ptc_login_nonce']) || !wp_verify_nonce($_POST['ptc_login_nonce'], 'ptc_login')) {
wp_die('Invalid request');
}
$creds = array(
'user_login' => sanitize_user($_POST['log'] ?? ''),
'user_password' => $_POST['pwd'] ?? '',
'remember' => !empty($_POST['rememberme'])
);
$user = wp_signon($creds, is_ssl());
if (is_wp_error($user)) {
wp_safe_redirect(wp_login_url() . '?login=failed');
exit;
}
wp_safe_redirect(admin_url());
exit;
}
add_action('admin_post_nopriv_ptc_login', 'ptc_handle_login');In your form, include a nonce:
<?php wp_nonce_field('ptc_login', 'ptc_login_nonce'); ?>This core-aligned pattern dramatically lowers the chance of Broken Authentication in WordPress via custom code.
2) Enforce HTTPS and secure cookies
Force SSL on admin and logins and prefer secure cookies:
// wp-config.php
define('FORCE_SSL_ADMIN', true);
if (strpos($_SERVER['HTTP_X_FORWARDED_PROTO'] ?? '', 'https') !== false) {
$_SERVER['HTTPS'] = 'on';
}
// Harden cookie behavior for plugins using PHP sessions
@ini_set('session.cookie_httponly', '1');
@ini_set('session.cookie_secure', '1');
@ini_set('session.use_only_cookies','1');
Set long, unique salts (rotate periodically):
// wp-config.php (use WordPress.org Salt generator)
define('AUTH_KEY', '...');
define('SECURE_AUTH_KEY', '...');
define('LOGGED_IN_KEY', '...');
define('NONCE_KEY', '...');
define('AUTH_SALT', '...');
define('SECURE_AUTH_SALT', '...');
define('LOGGED_IN_SALT', '...');
define('NONCE_SALT', '...');Security headers also help keep sessions safe:
// functions.php
add_action('send_headers', function () {
header('X-Frame-Options: SAMEORIGIN');
header('X-Content-Type-Options: nosniff');
header('Referrer-Policy: no-referrer-when-downgrade');
header('Permissions-Policy: interest-cohort=()');
header('Strict-Transport-Security: max-age=31536000; includeSubDomains; preload');
// Adjust CSP to your theme/plugins
header("Content-Security-Policy: default-src 'self' 'unsafe-inline' 'unsafe-eval' https: data:");
});These are foundational to preventing Broken Authentication from cookie theft and mixed-content issues.
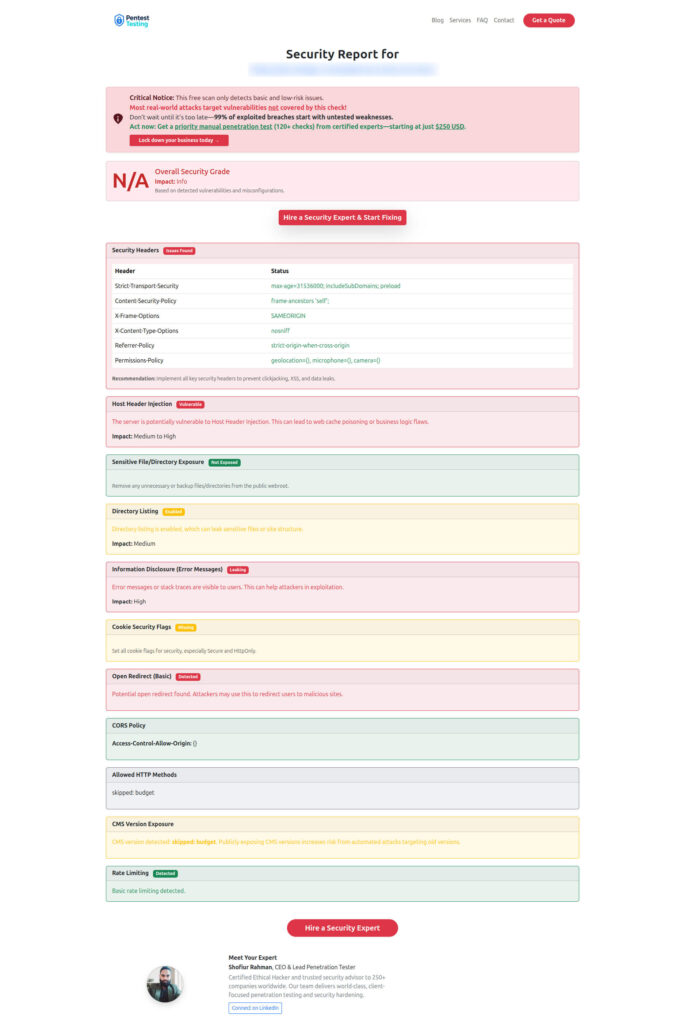
Screenshot of the free Website Vulnerability Scanner

3) Rate-limit brute force on /wp-login.php and xmlrpc.php
NGINX example:
limit_req_zone $binary_remote_addr zone=login:10m rate=10r/m;
server {
# ...
location = /wp-login.php {
limit_req zone=login burst=20 nodelay;
include fastcgi_params;
# ...
}
location = /xmlrpc.php {
limit_req zone=login burst=5 nodelay;
deny all; # or allowlist by IP if you must keep it
}
}Apache (.htaccess) allowlist example:
<Files "wp-login.php">
Require ip 203.0.113.10
Require ip 198.51.100.0/24
</Files>
<Files "xmlrpc.php">
Require all denied
</Files>Application-level limiter (Transients):
function ptc_brute_limit() {
$ip = $_SERVER['REMOTE_ADDR'] ?? 'unknown';
$key = 'ptc_login_' . md5($ip);
$attempts = (int) get_transient($key);
if ($attempts > 20) { // >20 attempts in 10 minutes? block.
status_header(429);
wp_die('Too many attempts. Try again later.');
}
set_transient($key, $attempts + 1, 10 * MINUTE_IN_SECONDS);
}
add_action('wp_login_failed', 'ptc_brute_limit');Every layer reduces the odds of Broken Authentication in WordPress via brute force.
4) Stop user enumeration (REST & errors)
Block public user listings that help password-guessing:
// Remove /wp-json/wp/v2/users endpoints
add_filter('rest_endpoints', function ($endpoints) {
unset($endpoints['/wp/v2/users']);
unset($endpoints['/wp/v2/users/(?P<id>[\d]+)']);
return $endpoints;
});
// Hide author archive lookups like /?author=1
add_action('template_redirect', function () {
if (is_author()) {
wp_redirect(home_url('/404'), 301);
exit;
}
});Custom error messages also help limit Broken Authentication reconnaissance:
add_filter('login_errors', fn() => __('Invalid credentials.', 'ptc'));
5) Harden password reset flows
Make resets CSRF-safe and enforce strong passwords:
// Enforce minimum password length & strength on reset
add_action('validate_password_reset', function ($errors) {
if (isset($_POST['pass1']) && strlen($_POST['pass1']) < 12) {
$errors->add('password_too_short', __('Use at least 12 characters.', 'ptc'));
}
}, 10, 1);Require nonces on custom reset forms:
// In form
<?php wp_nonce_field('ptc_reset', 'ptc_reset_nonce'); ?>
// In handler
if (!isset($_POST['ptc_reset_nonce']) || !wp_verify_nonce($_POST['ptc_reset_nonce'], 'ptc_reset')) {
wp_die('Invalid reset request');
}A sloppy reset handler is a common path to Broken Authentication in WordPress.
6) Add Two-Factor Authentication (2FA) hooks
You can implement TOTP-style checks (or integrate a vetted plugin). Minimal pseudo-implementation:
// After wp_signon succeeds, require OTP before finalizing session
add_action('wp_login', function ($user_login, $user) {
if (!ptc_otp_is_verified_for_request($user->ID)) {
// Store pending state and redirect to OTP form
wp_set_auth_cookie($user->ID, false); // temporary; consider flagging session
wp_safe_redirect(site_url('/otp-verify/'));
exit;
}
}, 10, 2);
// Example OTP check
function ptc_otp_is_verified_for_request($uid) {
// verify $_POST['otp'] against server-side TOTP secret for $uid
return isset($_SESSION['ptc_otp_ok']) && $_SESSION['ptc_otp_ok'] === true;
}Enforcing 2FA dramatically reduces Broken Authentication Issues from credential stuffing.
7) Kill old sessions on password change and on demand
// Force logout everywhere on password change
add_action('after_password_reset', function ($user) {
if (function_exists('wp_destroy_all_sessions')) {
wp_destroy_all_sessions();
}
});
// Provide a "Log out of other devices" button for users
if (is_user_logged_in() && function_exists('wp_destroy_other_sessions')) {
wp_destroy_other_sessions();
}This limits lateral movement after compromise—critical for Broken Authentication in WordPress incidents.
8) Disable XML-RPC (or lock it down)
add_filter('xmlrpc_enabled', '__return_false');If you need Jetpack or remote posting, restrict by IP or add authentication middleware to avoid Broken Authentication via XML-RPC pingbacks and multicall brute forcing.
9) Protect custom endpoints and admin-AJAX with nonces
// JS: include nonce
wp_localize_script('ptc-app', 'ptcAjax', [
'ajaxUrl' => admin_url('admin-ajax.php'),
'nonce' => wp_create_nonce('ptc_ajax'),
]);
// PHP: verify nonce for actions
add_action('wp_ajax_ptc_secure_action', 'ptc_secure_action');
add_action('wp_ajax_nopriv_ptc_secure_action', 'ptc_secure_action');
function ptc_secure_action() {
check_ajax_referer('ptc_ajax');
// ... handle action ...
wp_send_json_success(['ok' => true]);
}Nonces are essential to closing CSRF holes that often manifest as Broken Authentication.
10) Consider passwordless “magic links” for high-risk areas
// Send a one-time login link via email
function ptc_send_magic_link($user_id) {
$token = wp_generate_password(32, false);
update_user_meta($user_id, 'ptc_magic_' . $token, time());
$url = add_query_arg(['ptc_magic' => $token, 'uid' => $user_id], wp_login_url());
wp_mail(get_userdata($user_id)->user_email, 'Your secure sign-in link', "Click: $url\nThis link expires in 10 minutes.");
}
add_action('init', function () {
$token = $_GET['ptc_magic'] ?? '';
$uid = (int) ($_GET['uid'] ?? 0);
if ($token && $uid) {
$ts = (int) get_user_meta($uid, 'ptc_magic_' . $token, true);
if ($ts && (time() - $ts) < 600) {
delete_user_meta($uid, 'ptc_magic_' . $token);
wp_set_auth_cookie($uid, false, is_ssl());
wp_safe_redirect(admin_url());
exit;
}
}
});Properly implemented, magic links cut password reuse risk and help address Broken Authentication.
11) Monitor, alert, and test—continuously
- Log auth events (
wp_login,wp_login_failed) with IP, UA, and geolocation. - Alert on impossible travel (e.g., 1 hour: Dhaka → New York).
- Run regular scans.
After implementing the above, verify that Broken Authentication in WordPress is mitigated by scanning your site and reviewing the findings.
Sample Assessment report from our tool to check Website Vulnerability
Quick checklist to prevent Broken Authentication in WordPress
- Enforce HTTPS and strong salts.
- Rate-limit
/wp-login.phpand disable or restrictxmlrpc.php. - Use
wp_signon(); never compare raw passwords. - Hide REST user endpoints; generic login errors.
- Strong password policy + 2FA.
- Nonces on all state-changing forms/AJAX.
- Kill sessions on password change.
- Continuous monitoring + scans.
Each item cuts down pathways that lead to Broken Authentication in WordPress.
Related reading (deep dives & case studies)
- Strengthen your React front-end against caching pitfalls:
Web Cache Deception Attack in React.js — https://www.cybersrely.com/web-cache-deception-attack-in-react-js/ - Hardening WordPress object permissions:
Fix IDOR Vulnerability in WordPress — https://www.pentesttesting.com/fix-idor-vulnerability-in-wordpress/ - Don’t leak user data:
Sensitive Data Exposure in WordPress — https://www.pentesttesting.com/fix-sensitive-data-exposure-in-wordpress/ - PHP framework edge cases:
Web Cache Deception Attack in Laravel — https://www.pentesttesting.com/web-cache-deception-attack-in-laravel/ - Sector-specific:
Healthcare Software Penetration Testing — https://www.pentesttesting.com/healthcare-software-penetration-testing/
These topics often intertwine with Broken Authentication in WordPress, especially in multi-stack sites.
Our services (tailored help)
Managed IT Services for Security-First Ops
From patching to identity governance, our Managed IT Services team can implement the controls described here and watch over them 24/7.
👉 https://www.pentesttesting.com/managed-it-services/
AI Application Cybersecurity
If you’re integrating LLMs or AI features, we secure auth bridges between AI backends and WordPress to avoid novel session risks.
👉 https://www.pentesttesting.com/ai-application-cybersecurity/
Offer Cybersecurity Service to Your Client (White-Label)
Agencies can partner with us to deliver assessments, including checks for Broken Authentication in WordPress, under your brand.
👉 https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
Copy-paste snippets index
- Core login handler with nonce → Section 1
- HTTPS + secure cookies + salts → Section 2
- NGINX/Apache + Transients rate limiting → Section 3
- REST user endpoint removal + friendly errors → Section 4
- Password reset validation → Section 5
- 2FA hook scaffold → Section 6
- Session invalidation → Section 7
- Disable XML-RPC → Section 8
- AJAX nonces → Section 9
- Magic link login scaffold → Section 10
Final thoughts
The fastest path to reducing account takeovers is to standardize on WordPress’ built-in authentication APIs, enforce HTTPS and rate limiting, and layer 2FA and continuous monitoring. If any of this feels daunting—or if you suspect Broken Authentication in WordPress right now—run a free scan for Website Security test, then reach out. We’ll help you fix the gaps and keep your users safe.
Bonus: Developer-focused code guardrails
Block password reuse on reset (example):
add_action('profile_update', function ($user_id, $old_user_data) {
$new_hash = get_userdata($user_id)->user_pass;
$old_hash = $old_user_data->user_pass;
if ($new_hash === $old_hash) {
wp_die('Choose a new password.');
}
}, 10, 2);Short-lived JWT-style token for custom APIs (outline):
function ptc_issue_token($uid) {
$payload = ['uid' => $uid, 'exp' => time() + 900];
return base64_encode(json_encode($payload) . '|' . hash_hmac('sha256', json_encode($payload), AUTH_KEY));
}
function ptc_verify_token($token) {
[$b64, $sig] = explode('|', base64_decode($token));
return hash_equals(hash_hmac('sha256', $b64, AUTH_KEY), $sig) && json_decode($b64, true)['exp'] > time();
}Deny login for known breached passwords (outline using API result cached in transient):
add_filter('authenticate', function($user, $username, $password){
$key = 'ptc_pwned_' . md5($password);
$pwned = get_transient($key);
if ($pwned === false) {
// Call your internal/batched checker; store boolean for 1 day
$pwned = ptc_internal_pwned_lookup($password);
set_transient($key, $pwned ? '1' : '0', DAY_IN_SECONDS);
}
if ($pwned === '1') return new WP_Error('pwned', __('Choose a stronger password.'));
return $user;
}, 30, 3);Keep learning
Explore more posts and tutorials on our blog: https://www.pentesttesting.com/blog/ — including adjacent topics that often overlap with Broken Authentication in WordPress, like IDOR and cache deception.
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about Broken Authentication in WordPress.

Pingback: Prevent XML Injection in React.js: 10 Proven Ways