
SOC 2 Risk Assessment & Readiness Services
Build trust, reduce risk, and get audit-ready. Our SOC 2 Risk Assessment evaluates your controls against the Trust Services Criteria (Security, Availability, Confidentiality, Processing Integrity, Privacy) and gives you a prioritized roadmap to prepare for SOC 2 Type I/II.
⚖️ Why a SOC 2 Risk Assessment Matters
- Win enterprise deals: Buyers demand SOC 2 proof.
- Fewer audit surprises: Catch issues before your auditor does.
- Clear action plan: Risk-ranked fixes tied to the TSC.
- Faster Type I → Type II: Start with design (Type I), then evidence over time (Type II).
🧭 What’s Included in Our SOC 2 Risk Assessment
- TSC Mapping & Gap Analysis: Control-by-control evaluation across relevant criteria.
- Policy & Procedure Review: Security, access, change, vendor, incident, backups, logging, etc.
- Technical Control Review: Identity/SSO/MFA, endpoint, cloud (AWS/GCP/Azure), CI/CD, vuln mgmt.
- Risk Register & Prioritized Remediation Plan: Severity, effort, ownership, target dates.
- Evidence Readiness Guidance: Exactly what to collect for your auditor (screens, exports, tickets).
- Type I/Type II Path: Timeline and monitoring plan for a smooth SOC 2 Type II period.
🧩 Type I vs. Type II — Where to Start
- Type I: Are controls designed appropriately today? Snapshot readiness.
- Type II: Do controls operate effectively over 3–12 months? Operating evidence.
Most teams begin with Type I, then run the observation window for Type II.
🔍 How Our SOC 2 Assessment Process Works
1️⃣ Discovery & Scoping:
Systems, boundaries, vendors, data flows
2️⃣ Control Review:
Policies, procedures, tickets, and configurations
3️⃣ Evidence Check:
What exists vs. what auditors expect
4️⃣ Risk Ranking & Roadmap:
Gaps, owners, due dates, milestones
5️⃣ Readout & Next Steps:
Type I timeline, Type II readiness plan
🎯 Deliverables You Can Use Immediately
- SOC 2 Risk Assessment Report (executive + technical)
- Control Matrix mapped to Trust Services Criteria
- Risk Register with severity, owners, and dates
- Evidence Catalog (screens, exports, reports, tickets)
- Roadmap for Type I and the Type II observation window
⭐ Why Pentest Testing
- Compliance + Engineering: Practical controls that actually work.
- Audit-ready documentation: Built for how auditors review.
- Cross-framework leverage: Align with ISO 27001, HIPAA, PCI DSS where helpful.
- End-to-end support: From assessment to remediation to audit day.
Explore related services: Compliance & Risk Management Services and HIPAA Compliance Consulting for style parity.
🤝 Industries We Support
SaaS & Cloud, FinTech/Payments, HealthTech, AI/ML platforms, MSP/MSSP, Logistics, Marketplaces, DevTools.
⭐ What Our Clients Say
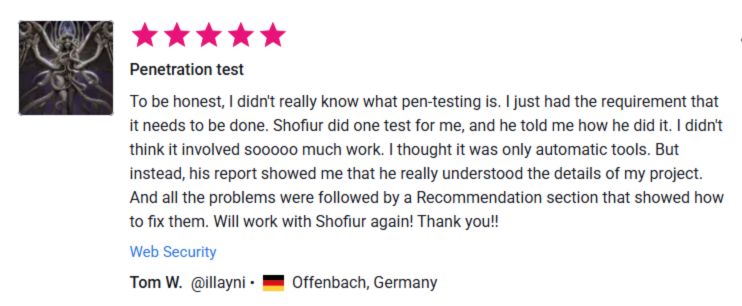

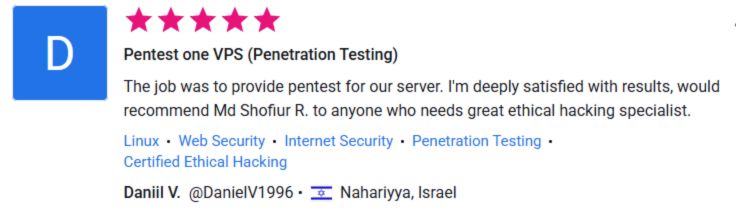
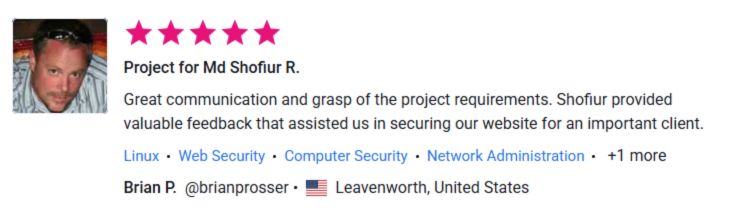
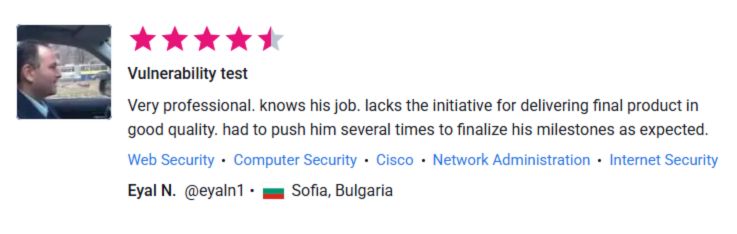
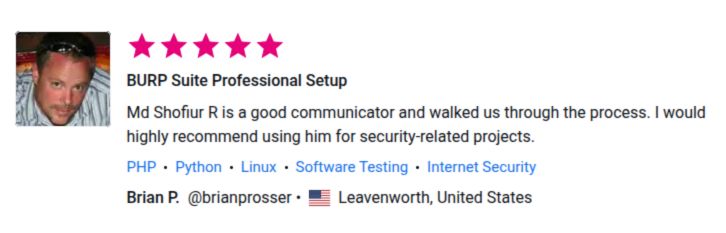
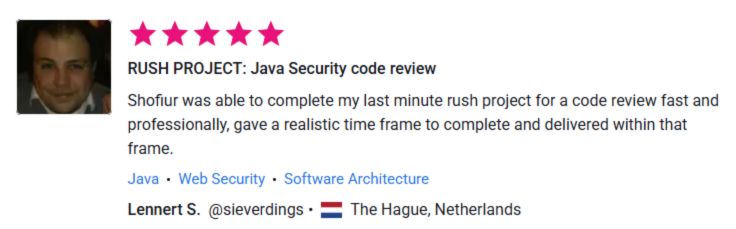
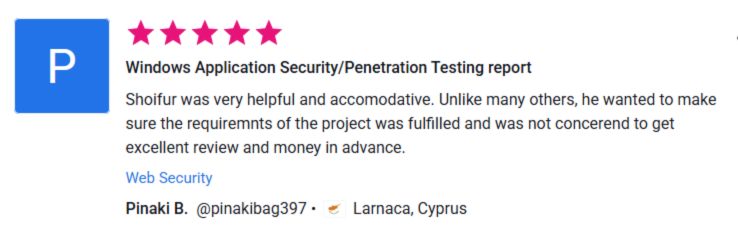
See More Client Results
Want to read more verified feedback and real-world outcomes from our engagements?
Explore our dedicated Testimonials page for detailed success stories across web, mobile, cloud, and AI app security.
Transparent Pricing:
We scope by size, complexity, and TSC in-scope. Book a quick call for a tailored quote.
Recent Case Studies
From vulnerability assessments to full-scale pentests — see how we deliver measurable impact.
Would you like to resell or refer our services to your clients?
👉 Learn more about our Cybersecurity Agency Partnership Program
https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about our products and services.
🚨 Need urgent investigation support?
If you’re seeing suspicious logins, malicious pop-ups, unknown apps, or ransomware activity, our Forensic Analysis Services can help you quickly validate compromise and secure your systems.
✅ Windows | macOS | Android | iOS | Email | Cloud ——— 👉 https://www.pentesttesting.com/digital-forensic-analysis-services/


