
ISO 27001 Risk Assessment Services
Find and prioritize risks to fast-track your certification.
Our ISO 27001 implementation support starts with a rigorous ISO 27001 risk assessment aligned to the 2022 edition—giving you a clear risk register, SoA inputs, and a treatment roadmap your auditor will love.
⚖️ Why ISO 27001 Risk Assessment Matters
A risk-based ISMS is the heart of ISO 27001. A formal, repeatable ISO 27001 risk assessment helps you:
- Reveal threats & vulnerabilities across people, process, and tech.
- Quantify risk (likelihood × impact) with defensible scoring.
- Map risks to Annex A controls and your Statement of Applicability (SoA).
- Prioritize remediation to reduce audit findings and speed certification.
✅ What You’ll Get (Deliverables)
- ISMS Scope Statement and context of the organization (internal/external issues, interested parties).
- Asset Inventory with data classification & owners.
- Risk Methodology (criteria, scales, acceptance thresholds).
- Risk Register (threats, vulnerabilities, existing controls, risk ratings).
- Risk Treatment Plan with control selection and owners/dates.
- Statement of Applicability (SoA) inputs mapped to Annex A (2022).
- Executive Summary for leadership & auditors.
- Roadmap with prioritized milestones and quick wins.
🧭 Our Risk Assessment Process
1️⃣ Discovery & Scoping:
Understand business processes, assets, and boundaries
2️⃣ Context & Assets:
Identify assets, data flows, and classification
3️⃣ Threats & Vulnerabilities:
Workshop + evidence review
4️⃣ Risk Evaluation:
Likelihood/impact scoring (e.g., 5×5), risk acceptance criteria
5️⃣ Control Mapping (Annex A):
Select/justify controls; prepare SoA inputs
6️⃣ Treatment Plan:
Owner, budget, timeline, evidence plan
7️⃣ Pre-Audit Readiness:
Findings walkthrough and auditor-style review
👥 Who We Help
- SaaS, FinTech, HealthTech & AI platforms
- E-commerce, Manufacturing, Logistics
- Government, Education & Non-profits
- MSPs, MSSPs, and cloud-native startups
⭐ Why Choose Pentest Testing Corp.
- Compliance + Security DNA: Real security, not just paperwork.
- Audit-Ready Artifacts: Registers, SoA inputs, and evidence mapped to clauses.
- Speed to Certification: Practical guidance, clear templates, and prioritized actions.
- From Gap to Cert: One partner from assessment to remediation and beyond.
Explore more: Compliance & Risk Management Services • Testimonials • Contact Us
⭐ What Our Clients Say
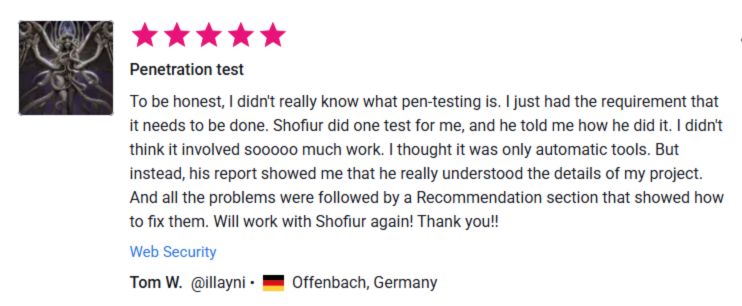

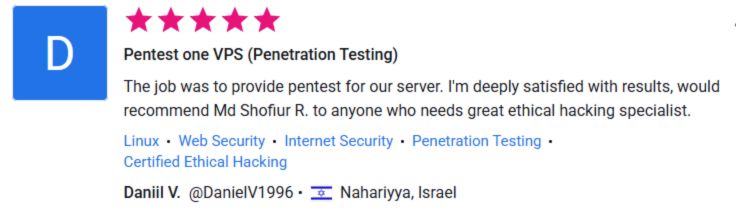
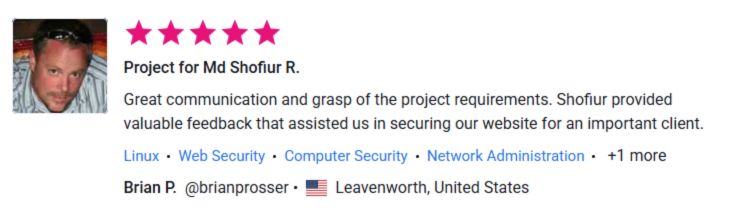
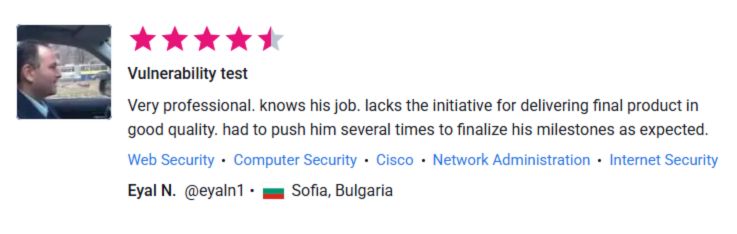
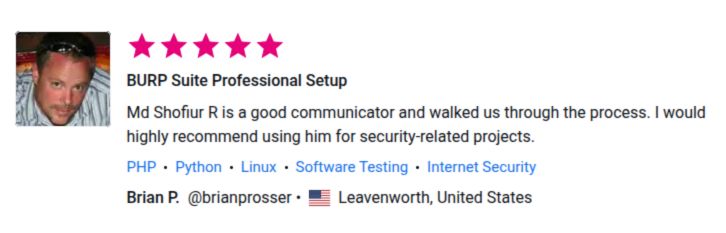
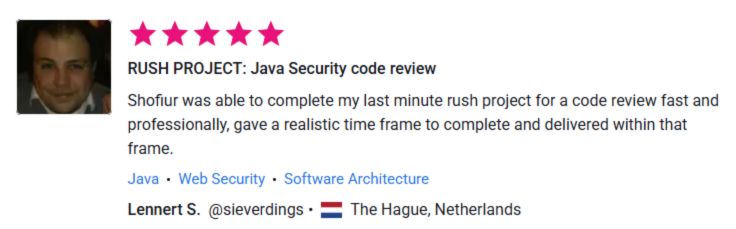
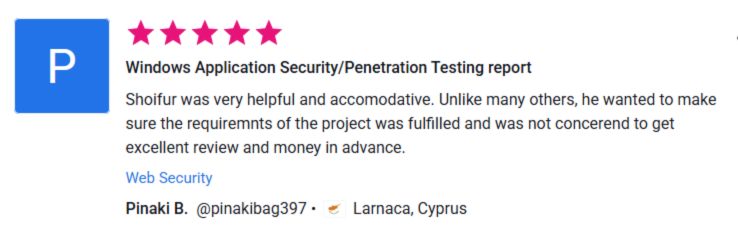
See More Client Results
Want to read more verified feedback and real-world outcomes from our engagements?
Explore our dedicated Testimonials page for detailed success stories across web, mobile, cloud, and AI app security.
Transparent Pricing:
Every business is unique. Contact us to get a customized quote based on your organization’s needs, infrastructure, and compliance requirements.
Recent Case Studies
From vulnerability assessments to full-scale pentests — see how we deliver measurable impact.
Would you like to resell or refer our services to your clients?
👉 Learn more about our Cybersecurity Agency Partnership Program
https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about our products and services.
🚨 Need urgent investigation support?
If you’re seeing suspicious logins, malicious pop-ups, unknown apps, or ransomware activity, our Forensic Analysis Services can help you quickly validate compromise and secure your systems.
✅ Windows | macOS | Android | iOS | Email | Cloud ——— 👉 https://www.pentesttesting.com/digital-forensic-analysis-services/


