7 Shocking Truths: Free Vulnerability Scanner Not Enough
Early-stage companies often run a free vulnerability scanner, see a mostly-green report, and assume they’re safe. But a free vulnerability scanner not enough once you have real users, real data, and real integrations.
Why? Because scanners can’t reliably validate the exact breach paths attackers prefer today: broken access control (IDOR/BOLA), role/permission flaws, business logic abuse, and third-party/API trust boundaries.
This post shows what free scanners do well, what they miss, and a budget-friendly next step that fits startup and SMB reality—plus copy/paste code patterns you can implement immediately.

Looking for an audit-friendly way to handle unsupported gear? Read our guide on EOL Network Devices: 7 urgent steps to find, score, contain, and replace unpatchable routers → https://www.pentesttesting.com/eol-network-devices-replacement-playbook/
Quick takeaways (save this)
- A green scan usually means “baseline hygiene looks OK,” not “breach-proof.”
- Most modern incidents come from authorization + logic + trust boundaries, not obvious misconfigurations.
- The best next move is often a targeted pentest sprint (auth + authorization + core flows + API abuse), not “boil-the-ocean” testing.
- You can reduce risk fast by centralizing authorization, adding policy checks, enforcing tenant/ownership in queries, and shipping security tests in CI.
1) Why startups & SMBs stop at free scanners
Startups and SMBs rely on free tools for good reasons:
- Budget pressure: security competes with product and growth.
- Speed: a scan runs in minutes.
- Triage avoidance: teams fear “too many findings.”
- False equivalence: “vulnerability scanning vs penetration testing” feels like the same thing, just deeper.
- Green report bias: people trust “passed” labels more than they should.
A free scan is useful—but it’s only one layer.
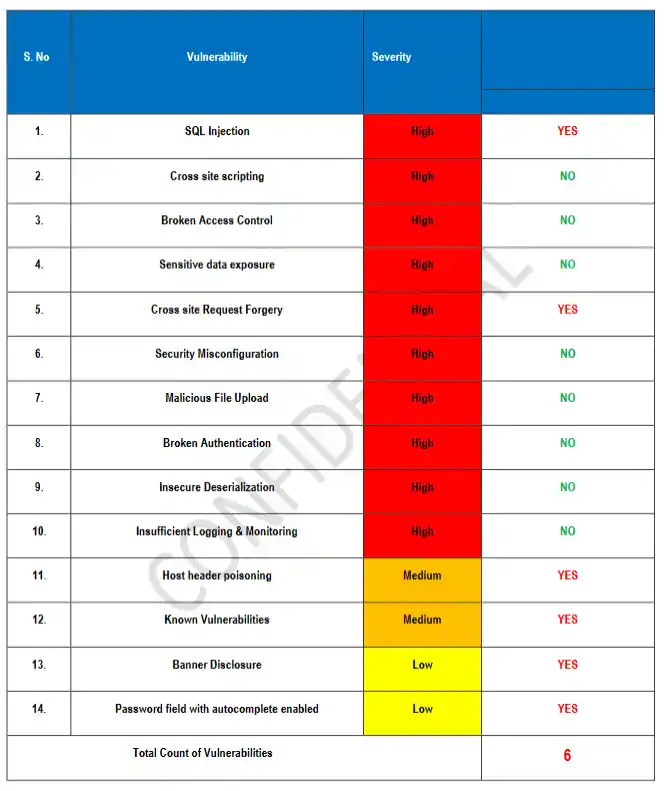
Free Website Vulnerability Scanner, use it as a strong baseline for security hygiene

2) What free scanners do well (and why you should keep using them)
A free vulnerability scanner is great for:
- HTTP security headers (HSTS, CSP, X-Frame-Options, etc.)
- Basic misconfigurations and exposed files/directories
- Weak cookie flags and common web hygiene issues
- Continuous monitoring/regressions (“something changed and now it’s worse”)
That’s valuable. Keep it in your routine.
Sample report from our security tool to check basic Website Vulnerability

3) What scanners miss most often (and attackers prioritize)
This is where “free vulnerability scanner not enough” becomes real.
A) Broken Access Control (IDOR/BOLA)
Scanners can’t prove that every API response is authorized for the caller—especially when it’s object-level (invoices, orders, files, tickets, tenants, orgs).
Real-world impact: data exposure across accounts/tenants, unauthorized actions, privilege escalation.
B) Role/permission flaws
“Admin-like” endpoints, inconsistent checks, legacy routes, or “support shortcuts” are common. Scanners don’t understand your intended permission model.
C) Business logic abuse
Discount abuse, workflow bypass, refund loops, race conditions, subscription tier bypass—these require human reasoning and end-to-end testing.
D) Trust boundaries (APIs, partners, webhooks, background jobs)
Many breaches happen through “valid” integrations:
- A compromised partner environment
- Over-permissive API keys
- Weak webhook validation
- Missing velocity controls on bulk endpoints
4) The “green report → breach” pattern (third-party API abuse)
A well-known example pattern is the 700Credit-style incident: attackers leveraged a compromised third-party integration pathway and abused API design/authorization gaps to access sensitive records at scale.
Why a scanner wouldn’t catch this end-to-end:
- The requests were authenticated and looked “normal”
- The weakness lived in authorization + partner trust boundaries
- The real failure was often scope/ownership checks + rate/velocity controls, not a simple signature-based vuln
This is exactly why a free vulnerability scanner not enough for API-first products, partner ecosystems, or SaaS with roles.
5) “Free scan → next step” bridge: the Startup Pentest Sprint
You don’t need to jump from “free scan” to a massive enterprise assessment.
A Startup Pentest Sprint (often 5–10 days) focuses on what automation misses:
- Auth + session handling
- Authorization (IDOR/BOLA) across top objects
- Top business flows (signup, billing, exports, admin, integrations)
- API abuse testing (scopes, pagination, bulk endpoints, rate limits)
- Proof-of-impact + prioritized remediation plan
Explore our dedicated services:
- https://www.pentesttesting.com/risk-assessment-services/
- https://www.pentesttesting.com/remediation-services/
- https://www.pentesttesting.com/api-pentest-testing-services/
- https://www.pentesttesting.com/web-app-penetration-testing-services/
6) Real-time fixes you can ship now (with code)
These patterns reduce the biggest gaps behind “free vulnerability scanner not enough”.
6.1 Centralize object-level authorization (IDOR/BOLA)
Node.js (Express) – authorize in the same query
// authz.js
async function authorizeInvoiceRead({ db, user, invoiceId }) {
// Enforce ownership/tenant scope in the lookup itself
const invoice = await db("invoices")
.where({ id: invoiceId, tenant_id: user.tenantId })
.first();
if (!invoice) return { allowed: false, status: 404 };
const roles = user.roles || [];
const ok = roles.includes("tenant_admin") || roles.includes("finance_read");
if (!ok) return { allowed: false, status: 403 };
return { allowed: true, invoice };
}
module.exports = { authorizeInvoiceRead };// routes.js
const { authorizeInvoiceRead } = require("./authz");
app.get("/api/invoices/:invoiceId", async (req, res, next) => {
try {
const user = req.user; // from auth middleware
const { invoiceId } = req.params;
const result = await authorizeInvoiceRead({ db, user, invoiceId });
if (!result.allowed) return res.sendStatus(result.status);
return res.json(result.invoice);
} catch (e) {
return next(e);
}
});Why this matters: checking ownership after fetching data is how IDOR slips in. Filter first.
6.2 FastAPI dependency pattern for authorization
from fastapi import Depends, HTTPException
def require_permission(permission: str):
def _dep(user=Depends(get_current_user)):
if permission not in user.permissions:
raise HTTPException(status_code=403, detail="Forbidden")
return user
return _dep
@app.get("/api/invoices/{invoice_id}")
def get_invoice(invoice_id: str, user=Depends(require_permission("invoice:read"))):
invoice = db.get_invoice(invoice_id, tenant_id=user.tenant_id) # tenant-scoped fetch
if not invoice:
raise HTTPException(status_code=404, detail="Not found")
return invoice6.3 Policy-as-code to prevent authorization drift
OPA/Rego example
package authz
default allow = false
allow {
input.action == "invoice:read"
input.resource.tenant_id == input.subject.tenant_id
some r
r := input.subject.roles[_]
r == "tenant_admin" or r == "finance_read"
}6.4 Enforce tenant isolation at the database layer (PostgreSQL RLS)
ALTER TABLE invoices ENABLE ROW LEVEL SECURITY;
-- Each request sets: SET LOCAL app.current_tenant_id = '...';
CREATE POLICY tenant_isolation_invoices ON invoices
USING (tenant_id = current_setting('app.current_tenant_id')::uuid);6.5 Verify webhooks (trust boundary hardening)
import hmac, hashlib
def verify_webhook(raw_body: bytes, header_sig: str, secret: str) -> bool:
expected = hmac.new(secret.encode(), raw_body, hashlib.sha256).hexdigest()
return hmac.compare_digest(expected, header_sig)6.6 Rate limit the endpoints attackers can “abuse legitimately”
const rateLimit = require("express-rate-limit");
const exportLimiter = rateLimit({
windowMs: 60 * 1000,
max: 30,
standardHeaders: true,
legacyHeaders: false,
});
app.use("/api/exports", exportLimiter);6.7 Put security tests in CI (the scanner can’t do this for you)
def test_cross_tenant_invoice_access(client_tenant_a, client_tenant_b, invoice_id_a):
r = client_tenant_b.get(f"/api/invoices/{invoice_id_a}")
assert r.status_code in (403, 404)
def test_export_requires_privilege(client_user, client_admin):
assert client_user.post("/api/exports/invoices").status_code == 403
assert client_admin.post("/api/exports/invoices").status_code in (200, 202)6.8 Detect “shadow endpoints” with OpenAPI diffs
import json
from pathlib import Path
old = json.loads(Path("openapi.prev.json").read_text())
new = json.loads(Path("openapi.json").read_text())
added = sorted(set(new.get("paths", {})) - set(old.get("paths", {})))
if added:
print("New API paths detected (security review required):")
for p in added:
print(" -", p)
raise SystemExit(1)7) Decision matrix: when scanning is enough vs when you need more
| Situation | Scan only | Targeted sprint | Full pentest |
|---|---|---|---|
| Static marketing site, no auth, no PII | Often | Optional | Rare |
| SaaS app with login + roles | Not enough | Best fit | Sometimes |
| API-first + integrations/partners | Not enough | Best fit | Often |
| Fundraising / enterprise deals / compliance | Not enough | Maybe | Best fit |
| Major release (auth, billing, export, admin) | Not enough | Best fit | Sometimes |
If you’re unsure, start with a scoped plan via:
Then move fast on fixes with:
8) Related reads from our blog
- https://www.pentesttesting.com/multi-tenant-saas-breach-containment/
- https://www.pentesttesting.com/ai-cloud-security-risks-modern-pentest/
- https://www.pentesttesting.com/misconfigured-edge-devices-hardening-sprint/
Final Thought: Scanning Is Visibility—Not Assurance
If you’re relying on a free vulnerability scanner today, keep it—and add human validation where breaches actually happen: authorization, business logic, and trust boundaries.
Start here:
- https://www.pentesttesting.com/api-pentest-testing-services/
- https://www.pentesttesting.com/web-app-penetration-testing-services/
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about Scanning vs Penetration Testing.