Crypto Smart Contract Unlock Scam: $30k Trap
The new twist on an old con: the crypto smart contract unlock scam
If someone tells you there’s a smart contract “holding $29,000,000 for you” and you must pay $30,000 to “unlock funds” with a secret code, you’re looking at a classic advance-fee play wrapped in tech jargon. In the case study behind this article, scammers used LINE/iMessage to send code snippets and screenshots labeled “contract,” “secret phrase,” “deadline,” and “withdraw”—all to convince the victim that a big payout was one small “verification fee” away. That pressure escalated with messages like “this is the final bus stop… after payment in less than 1 hour it’s all over.”
This pattern isn’t new; it’s the same psychology as lottery and inheritance scams—only now the bait is blockchain and Solidity.
Audit tip — NIST SP 800-53 5.2 remediation evidence checklist: https://www.pentesttesting.com/nist-sp-800-53-5-2/
How the scam works (step-by-step)
- Contact & credibility theatre (LINE/Telegram/WhatsApp).
A “recovery agent” or “friend” claims they can recover funds lost in a prior trading scam. They share screenshots and pseudo-technical explanations to build trust. - The fake technical proof.
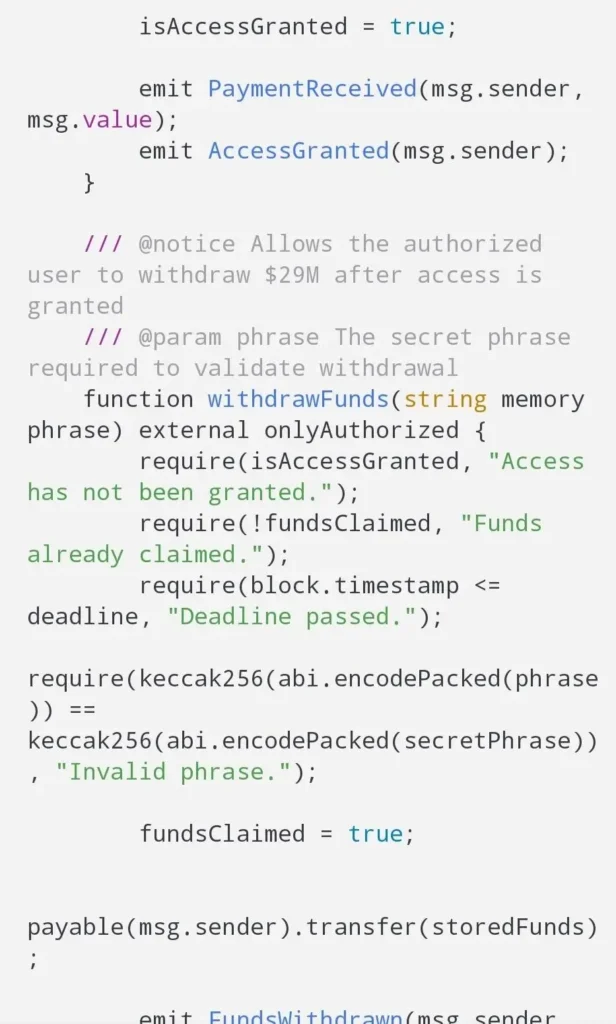
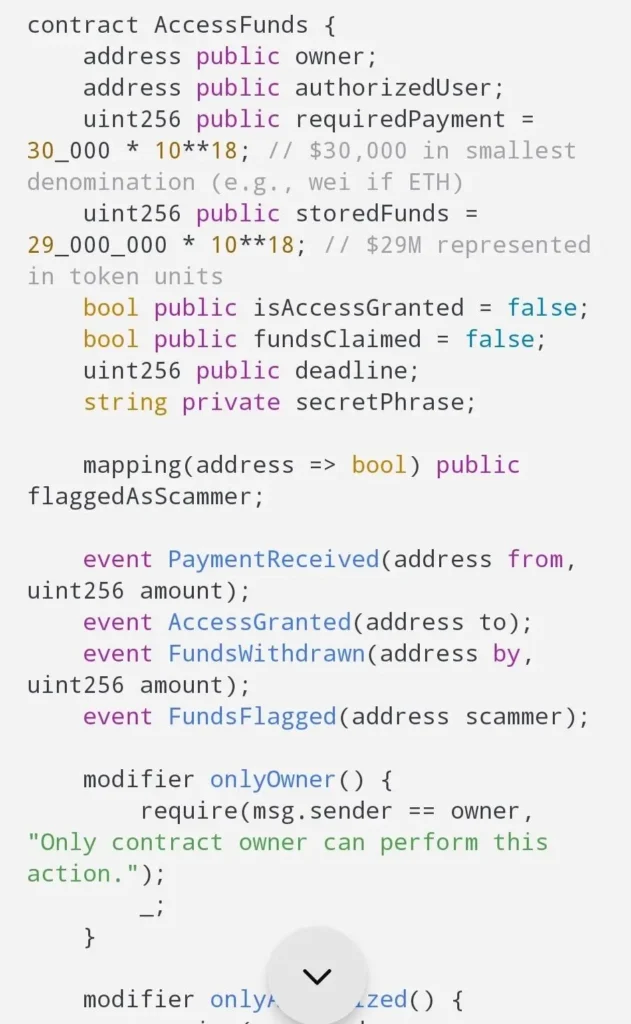
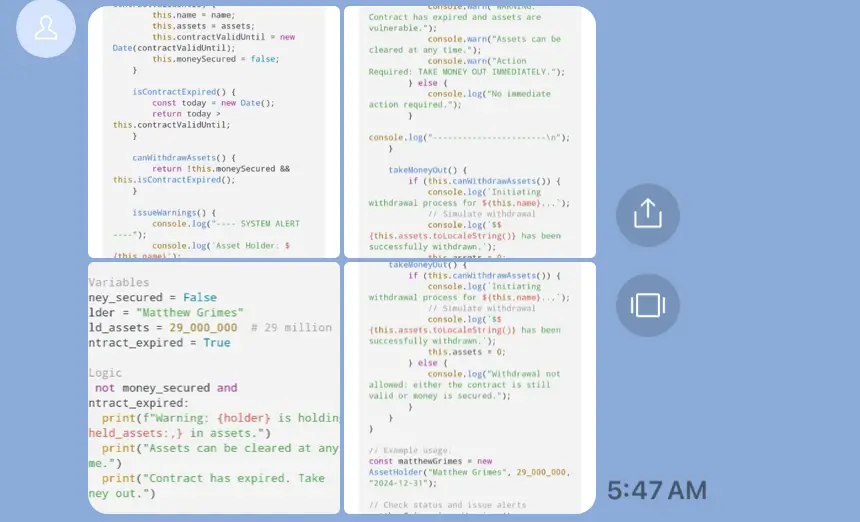
You’re shown snippets that look like Solidity or JavaScript with variable names likeheld_assets = 29_000_000, flags such ascontract_expired = True, and functions namedwithdrawFunds()orflagUnclaimedFunds(). It looks real—but it’s marketing cosplay, not verifiable code.
- The hook: an unlock code fee.
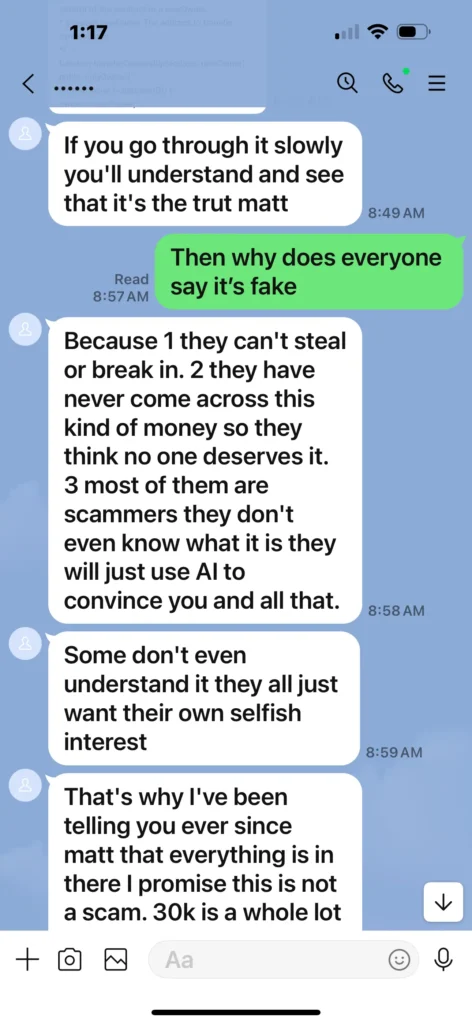
You’re told only you (or their “authorized user”) can pay $30,000 to triggerAccessGrantedand release the funds. They insist partial payments won’t work, and add urgency with made-up “deadlines.” - Pressure & isolation.
When you hesitate, they claim critics “don’t understand blockchain,” or are “scammers” themselves. They’ll say things like “others just use AI to convince you” and insist only they can help.
- Exit or escalation.
If you pay, the goalposts move—more “fees,” “taxes,” or “gas” costs appear. If you refuse, they ghost you or threaten that the “contract will mark you as a scammer” if not paid—pure fiction.
Technical red flags in these Solidity contract scam attempts
- Off-chain “secret phrases.”
Real smart contracts don’t rely on private chat “codes.” Contract logic lives on-chain and is auditable. - Owner-only power over your payout.
Screens likemodifier onlyOwner()and “admin withdraw” are dead giveaways. If a single wallet owner controls release, it’s not a trustless escrow—it’s a custodial honeypot. - Unverifiable source.
Legit projects verify their contract source on Etherscan/Polygonscan. If you can’t find a publicly verified contract address and code, assume it’s fake. - Impossible economics.
No legitimate protocol requires a $30k prepayment to move money “you already own.” That’s an advance fee crypto scam, full stop.
Quick reality checks you (or a friend) can run
- Ask for the contract address and chain.
Then check the address on a block explorer. Is the source verified? Does the contract even contain a function that could do what they claim? - Demand cryptographic proof of control.
A real “recovery agent” who controls funds can:- Sign a message from the fund-holding address, or
- Send a small dust test outbound to an address you control.
Scammers will dodge both.
- Follow the money.
Look at the transaction history on the explorer. Are there any inbound transfers matching the story? Any prior “unlock fees” being drained to the same set of wallets? - Never pay to unlock money.
If payment is required first—it’s a scam. There are no special off-chain codes, no “admin dashboards,” and no magical support routes that bypass custody policies at exchanges.
What to do if you’re targeted
- Stop all payments and cut contact.
Block the “agent” on every platform. - Preserve evidence.
Save chats, wallet addresses, domains, and any “fee” instructions. - Report the infrastructure.
File abuse reports for the domain/hosting and report wallet addresses to your exchange and chain analytics hotlines. - Tell your story.
Awareness prevents loss. We documented a related scheme in our case study on a Telegram job fraud—worth sharing with friends and family who are at risk.
Read: Oka-Furniture.com Telegram Job Scam — A Real-Life Case Study.
Can a cybersecurity team help with this?
Yes—before you invest anywhere, have a professional vet the platform’s app, APIs, and smart-contract claims. Our team performs deep manual testing of web apps and APIs (business logic + OWASP), validates claims, and gives you plain-English risk calls.
→ Learn more: Expert Web App Penetration Testing Services.
Final checklist to avoid a crypto smart contract unlock scam
- Never pay any “unlock code fee,” “tax,” or “verification” to release funds.
- Demand the contract address and verify source code on the explorer.
- Require a signed message or dust test from the fund-holding address.
- If in doubt, get an independent security review—or walk away.
Attribution & context
This article was prepared from real client communications/screenshots involving LINE/iMessage pressure tactics, fake code snippets (including Solidity-style functions like withdrawFunds/onlyOwner), and a $30k advance-fee demand—hallmarks of the Solidity contract scam pattern.
Need a quick, confidential review of a platform before you send money?
Book a rapid assessment with Pentest Testing Corp and we’ll tell you—clearly—if what you’re seeing is safe, risky, or a scam.
—
Related reading: Oka-Furniture.com Telegram Job Scam — A Real-Life Case Study
Services: Expert Web App Penetration Testing Services