
SOC 2 Remediation Services — Fix Compliance Gaps
Risk assessments reveal issues. Our SOC 2 Remediation Services implement the fixes, produce audit-ready evidence, and guide you from Type I into a successful Type II reporting period.
🚨 Why Remediation Is Critical
- Audits need proof: Controls must be implemented and evidenced.
- Reduce breach risk: Close identity, access, vendor, and cloud gaps.
- Accelerate deals: Shorten security questionnaires with SOC 2 coverage.
- Stay aligned: Keep controls effective through the Type II window.
🛠️ Our SOC 2 Remediation Services
- Policy & Documentation Updates – Security, access, change mgmt, incident, vendor, SDLC.
- Technical Safeguards – SSO/MFA baselines, least privilege, logging, SIEM, backups, EDR, patching.
- Cloud Hardening – CIS benchmarks, network segmentation, secrets, key mgmt, IaC guardrails.
- Vendor & Third-Party – Risk ratings, due diligence, contracts, monitoring.
- Incident Response – Runbooks, tabletop exercises, lessons learned.
- Evidence & Validation – Tickets, screenshots, exports, monitoring proofs for the auditor.
🧱 Common Issues We Remediate
- Missing/legacy policies, undefined ownership
- Inconsistent access reviews or admin sprawl
- Unmonitored logs, alerting gaps, weak vuln mgmt
- Unencrypted data stores, weak key rotation
- Shadow/SaaS sprawl and vendor due diligence gaps
- No change management trail for releases
🔁 How Remediation Works
1️⃣ Prioritize Findings:
Severity, audit impact, and effort
2️⃣ Implement Controls:
Policy + technical workstreams in parallel
3️⃣ Train & Operationalize:
Who does what, how often, where it’s recorded
4️⃣ Collect Evidence:
Tickets, screenshots, exports, reports
5️⃣ Validate & Sign-off:
Internal verification + auditor-ready packet
📑 Deliverables
- Remediation Plan & Tracker with owners and dates
- Updated Policies/Procedures and Runbooks
- Config baselines (e.g., IAM, logging, backups, vuln mgmt)
- Evidence Pack (screens, logs, exports, tickets)
- Validation Report for your auditor and stakeholders
⭐ Why Pentest Testing
- Engineers + GRC consultants working together
- Auditor-friendly artifacts without the busywork
- Reusable controls that map to ISO 27001, HIPAA, PCI DSS
- Clear communication, milestones, and sign-offs
See also: Compliance & Risk Management Services and HIPAA Remediation Services.
⭐ What Our Clients Say
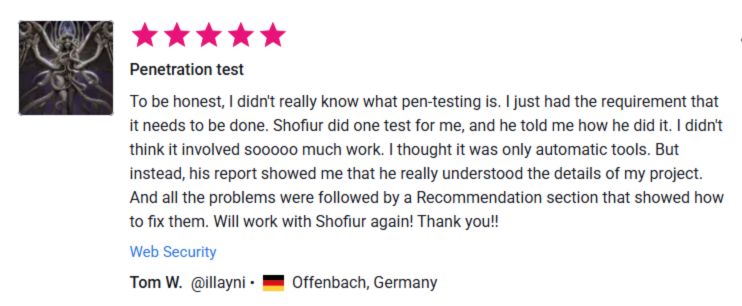

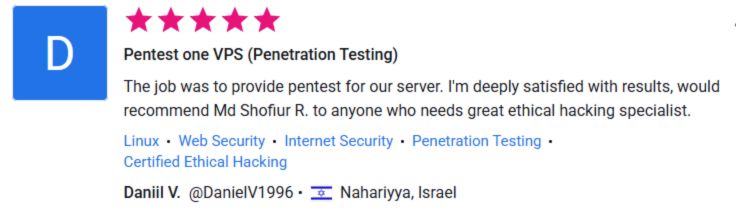
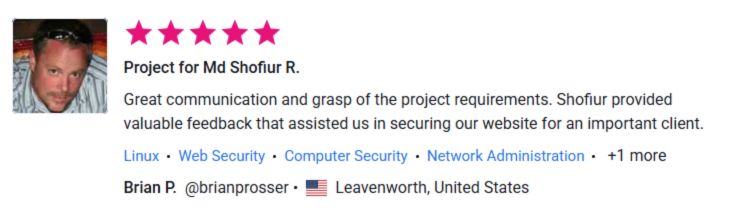
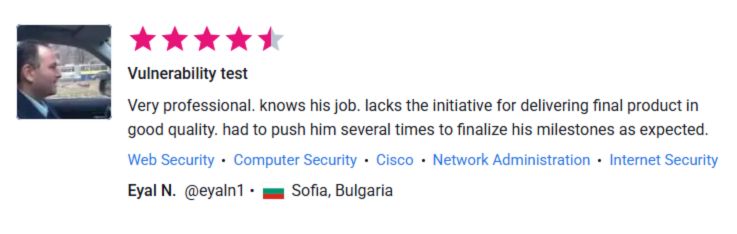
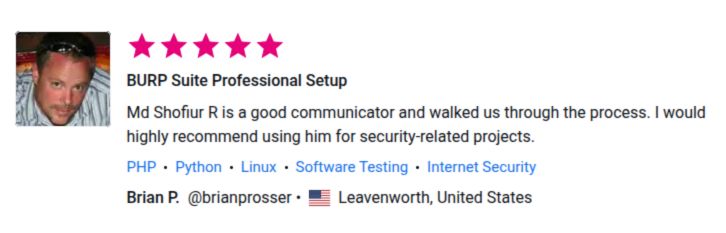
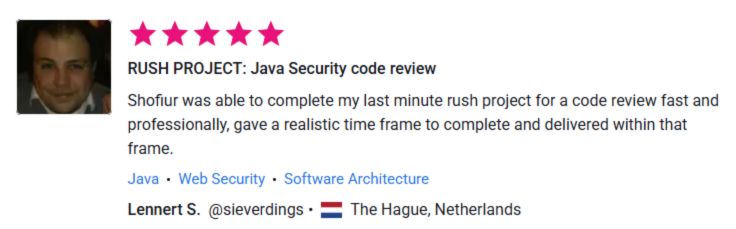
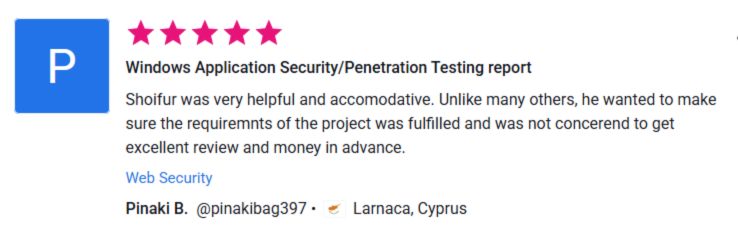
See More Client Results
Want to read more verified feedback and real-world outcomes from our engagements?
Explore our dedicated Testimonials page for detailed success stories across web, mobile, cloud, and AI app security.
Transparent Pricing:
Pricing is scoped to size, complexity, and in-scope criteria. Quick call = accurate quote.
Recent Case Studies
From vulnerability assessments to full-scale pentests — see how we deliver measurable impact.
Would you like to resell or refer our services to your clients?
👉 Learn more about our Cybersecurity Agency Partnership Program
https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about our products and services.
🚨 Need urgent investigation support?
If you’re seeing suspicious logins, malicious pop-ups, unknown apps, or ransomware activity, our Forensic Analysis Services can help you quickly validate compromise and secure your systems.
✅ Windows | macOS | Android | iOS | Email | Cloud ——— 👉 https://www.pentesttesting.com/digital-forensic-analysis-services/


