Broken Access Control in WordPress: 7 Proven Ways to Fix It
If your WordPress site lets the wrong people read, edit, or delete what they shouldn’t, you’re dealing with Broken Access Control. It’s one of the most exploited issues on real sites because it hides in plain sight—missing capability checks, insecure AJAX/REST endpoints, weak role setups, or files that are directly reachable without authorization. In this guide, you’ll get a practical, human-written walkthrough with copy-paste-ready code to detect and fix these risks—plus a checklist you can run after every feature release.

Who is this for? WordPress developers, plugin/theme authors, and site owners who want to prevent IDOR, privilege escalation, and unauthorized data exposure.
TL;DR Checklist (Quick Wins)
- Audit roles/capabilities; remove “admin-like” rights from non-admin roles.
- Add
current_user_can()checks to every privileged action. - Secure AJAX and REST routes with capability checks + nonces.
- Prevent IDOR by verifying ownership or capabilities before loading records.
- Block direct access to sensitive uploads with .htaccess/nginx rules.
- Add server-side guards (
template_redirect,pre_get_posts,map_meta_cap). - Re-test with an external scanner and manual misuse cases.
Tip: Keep the phrase Broken Access Control on your team’s “release checklist” so every new feature gets the right guards.
1) Fix Role & Capability Design (Foundation for Everything)
Poor role design leads to Broken Access Control in WordPress, even when individual features are coded “okay.” Start by creating least-privilege roles and granting only what’s necessary.
Create a Minimal Editor-Like Role (code example)
// mu-plugins/roles-bootstrap.php (auto-load under wp-content/mu-plugins)
<?php
add_action('init', function () {
$role = get_role('content_manager');
if (!$role) {
$role = add_role('content_manager', 'Content Manager', [
'read' => true,
'edit_posts' => true,
'edit_published_posts' => true,
'publish_posts' => true,
'upload_files' => true,
]);
}
// Ensure we do NOT accidentally grant admin-like caps:
$dangerous = ['manage_options','edit_users','delete_users','install_plugins','activate_plugins','edit_themes'];
foreach ($dangerous as $cap) {
if ($role && $role->has_cap($cap)) {
$role->remove_cap($cap);
}
}
});Why it helps: Thoughtful roles cut the blast radius. Many “Broken Access Control” incidents start with overly broad capabilities.
2) Always Check Capabilities on Admin Pages & Actions
Any admin page or operation that changes data must enforce capabilities server-side.
Secure Custom Admin Page
add_action('admin_menu', function () {
add_menu_page(
'Project Tools',
'Project Tools',
'manage_options', // capability required
'project-tools',
function () {
if (!current_user_can('manage_options')) {
wp_die(__('Unauthorized.'));
}
echo '<div class="wrap"><h1>Project Tools</h1></div>';
}
);
});Use a specific capability (e.g.,
manage_project_tools) instead of a generic one. Map it withmap_meta_cap(shown later).
3) Prevent IDOR: Verify Ownership + Capability
IDOR (Insecure Direct Object Reference) is a classic Broken Access Control in WordPress flaw—users access someone else’s record by guessing IDs.
Vulnerable (don’t do this)
// ?doc_id=123
$doc_id = absint($_GET['doc_id'] ?? 0);
$doc = get_post($doc_id); // Custom post type "doc"
echo wp_kses_post($doc->post_content); // ❌ no authorization!Safe Version
$doc_id = absint($_GET['doc_id'] ?? 0);
$doc = get_post($doc_id);
if (!$doc) {
wp_die('Not found');
}
// Enforce ownership OR a specific capability:
if ((int)$doc->post_author !== get_current_user_id() &&
!current_user_can('edit_post', $doc_id)) {
wp_die('Unauthorized');
}
echo wp_kses_post($doc->post_content);Pattern to remember: Enforce ownership or a granular capability before returning data. That’s how you avoid Broken Access Control in WordPress routes.
4) Secure AJAX Endpoints with Nonces + Caps
Vulnerable AJAX (common in plugins)
add_action('wp_ajax_export_data', function () {
// ❌ no nonce, no capability check
$export = my_generate_export();
wp_send_json_success($export);
});Hardened AJAX
add_action('wp_ajax_export_data', function () {
check_ajax_referer('export_data_nonce'); // CSRF defense
if (!current_user_can('export_site_data')) { // Granular cap
wp_send_json_error(['message' => 'Unauthorized'], 403);
}
$export = my_generate_export();
wp_send_json_success($export);
});
// Enqueue script with nonce
add_action('admin_enqueue_scripts', function ($hook) {
if ('toplevel_page_project-tools' !== $hook) return;
wp_enqueue_script('project-tools', plugins_url('tools.js', __FILE__), ['jquery'], null, true);
wp_localize_script('project-tools', 'ProjectTools', [
'ajaxUrl' => admin_url('admin-ajax.php'),
'nonce' => wp_create_nonce('export_data_nonce'),
]);
});Client call (JS):
jQuery.post(ProjectTools.ajaxUrl, {
action: 'export_data',
_ajax_nonce: ProjectTools.nonce
}).done(res => {
if (res.success) console.log('Export ready', res.data);
});This pattern alone eliminates a huge chunk of Broken Access Control in WordPress from AJAX handlers.
5) Lock Down REST API Routes (permission_callback)
The REST API is powerful—and a frequent source of Broken Access Control in WordPress when permission_callback is missing or too permissive.
Proper Route Registration
add_action('rest_api_init', function () {
register_rest_route('proj/v1', '/report/(?P<id>\d+)', [
'methods' => 'GET',
'callback' => function (WP_REST_Request $req) {
$id = (int) $req['id'];
$post = get_post($id);
if (!$post) {
return new WP_Error('not_found', 'Not found', ['status' => 404]);
}
// Enforce ownership OR capability:
if ((int)$post->post_author !== get_current_user_id() &&
!current_user_can('read_post', $id)) {
return new WP_Error('forbidden', 'Unauthorized', ['status' => 403]);
}
return [
'id' => $id,
'title' => get_the_title($id),
'content' => apply_filters('the_content', $post->post_content),
];
},
'permission_callback' => function (WP_REST_Request $req) {
$id = (int) $req['id'];
// Only logged-in users with read access (cap/ownership) may proceed:
return is_user_logged_in() && (
(int)get_post_field('post_author', $id) === get_current_user_id()
|| current_user_can('read_post', $id)
);
},
]);
});6) Enforce Access at the Query Layer (pre_get_posts)
Even if templates forget checks, you can centralize access control with pre_get_posts to avoid Broken Access Control for custom lists.
add_action('pre_get_posts', function (WP_Query $q) {
if (is_admin() || !$q->is_main_query()) return;
// Example: Only show "project" CPT entries that belong to the user,
// unless the user can 'read_private_projects'
if ($q->is_post_type_archive('project')) {
if (!current_user_can('read_private_projects')) {
$q->set('author', get_current_user_id());
$q->set('post_status', ['publish']); // no private posts
}
}
});7) Map Meta Capabilities for Fine-Grained Control
Use map_meta_cap to decide who can do what at runtime.
add_filter('map_meta_cap', function ($caps, $cap, $user_id, $args) {
if ($cap === 'export_site_data') {
// Only admins or users with a custom flag can export
if (user_can($user_id, 'manage_options') || get_user_meta($user_id, 'can_export', true)) {
return ['exist']; // allow
}
return ['do_not_allow']; // deny
}
if ($cap === 'read_post' && !empty($args[0])) {
$post_id = (int) $args[0];
$post_author = (int) get_post_field('post_author', $post_id);
if ($post_author === $user_id || user_can($user_id, 'edit_post', $post_id)) {
return ['exist'];
}
return ['do_not_allow'];
}
return $caps;
}, 10, 4);This is a powerful way to prevent Broken Access Control in WordPress everywhere the capability is checked.
8) Block Direct File Access (.htaccess / Nginx)
Media or exported reports stored under /uploads/private/ should never be downloadable by guessing URLs.
Apache (.htaccess)
# wp-content/uploads/private/.htaccess
Order Allow,Deny
Deny from allOr modern Apache:
Require all deniedNginx
location ^~ /wp-content/uploads/private/ {
deny all;
return 403;
}Serve files through a proxy PHP that checks current_user_can() or ownership before streaming.
// secure-download.php
<?php
require_once dirname(__FILE__, 3) . '/wp-load.php';
if (!is_user_logged_in()) {
status_header(403);
exit('Forbidden');
}
$rel = sanitize_text_field($_GET['file'] ?? '');
$path = realpath(WP_CONTENT_DIR . '/uploads/private/' . $rel);
if (!$path || !str_starts_with($path, WP_CONTENT_DIR . '/uploads/private/')) {
status_header(404);
exit('Not found');
}
// Check capability/ownership here...
if (!current_user_can('read_private_reports')) {
status_header(403);
exit('Unauthorized');
}
header('Content-Type: application/octet-stream');
readfile($path);9) Template Guardrails (template_redirect)
add_action('template_redirect', function () {
if (is_page('team-dashboard') && !current_user_can('read_private_pages')) {
auth_redirect(); // send to login if not authorized
}
});This prevents a whole class of Broken Access Control where template conditions accidentally expose content.
10) Admin Actions Need Nonces (check_admin_referer)
// Form
wp_nonce_field('delete_customer_nonce', 'delete_customer_nonce');
// Handler
if (!isset($_POST['delete_customer_nonce']) ||
!wp_verify_nonce($_POST['delete_customer_nonce'], 'delete_customer_nonce')) {
wp_die('Invalid request');
}
if (!current_user_can('delete_customer', $customer_id)) {
wp_die('Unauthorized');
}Nonces stop CSRF. Capability checks stop Broken Access Control in WordPress.
11) WP-CLI Audits (DevOps Friendly)
# List users & roles
wp user list --fields=ID,user_login,roles
# Search for suspicious caps in DB
wp eval "global $wp_roles; print_r( $wp_roles->roles );"
# Grep codebase for dangerous patterns (rough checks)
grep -R \"wp_ajax_\" wp-content | grep -v \"check_ajax_referer\"
grep -R \"register_rest_route\" wp-content | grep -v \"permission_callback\"These quick commands find hotspots that commonly cause Broken Access Control in WordPress.
How to Test Your Fixes (Manual + Automated)
- Role hopping: Try a low-privilege account; visit admin pages, AJAX routes, and REST endpoints.
- IDOR attempts: Change numeric IDs in URLs/requests. You should see “Unauthorized.”
- Direct files: Hit
/wp-content/uploads/private/...directly. Expect 403. - Scanner pass: Run an external scan to catch common access flaws you missed.
Screenshot of the Pentest Testing Corp Free Website Vulnerability Scanner

Sample Vulnerability Report by the free tool to check Website Vulnerability
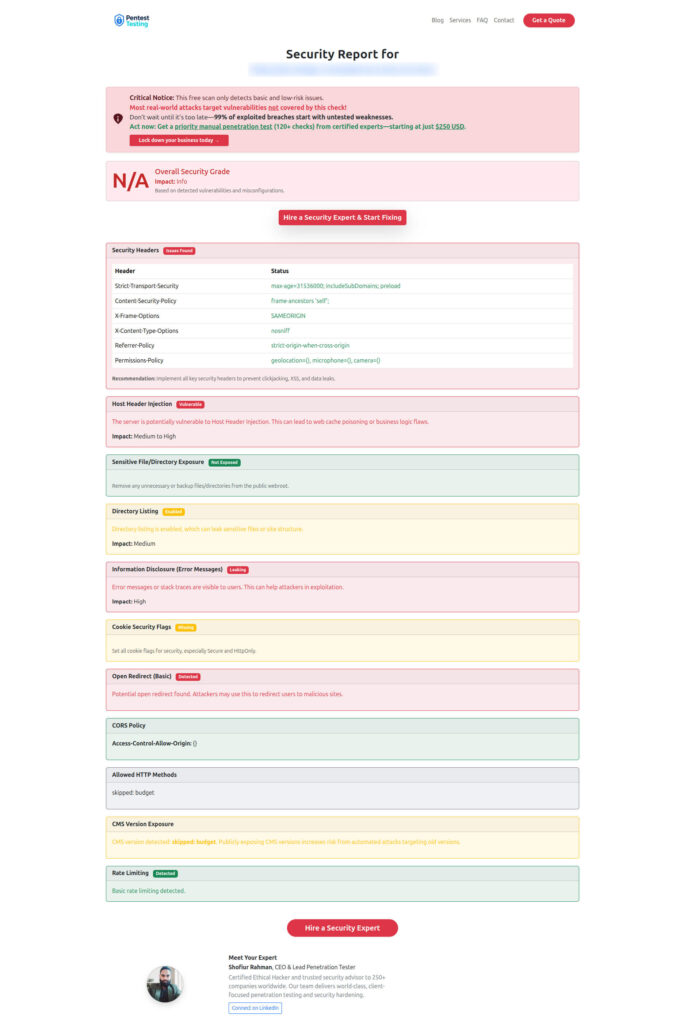
Use the free scanner often to avoid regressions and to surface new areas of Broken Access Control as your WordPress site evolves.
Related Case Studies & Deep Dives
- Real-world plugin exposure: Healthcare Plugin Exploit — see how weak checks lead to data leaks and how we fixed them the right way.
👉 pentesttesting.com/healthcare-plugin-exploit/ - App-layer auth issues: Prevent Weak API Authentication in Laravel
👉 pentesttesting.com/prevent-weak-api-authentication-in-laravel/ - Hardening frameworks: Fix Security Misconfigurations in Laravel
👉 pentesttesting.com/fix-security-misconfigurations-in-laravel/ - WordPress Exploitation: Stop RCE Exploits in WordPress
👉 https://www.pentesttesting.com/stop-rce-exploits-in-wordpress/ - Case Study: Rapid Incident Response for a Japanese Healthcare Website
👉 https://www.pentesttesting.com/healthcare-plugin-exploit/ - Frontend auth pitfalls: Weak API Authentication in React.js (partner blog)
👉 cybersrely.com/weak-api-authentication-in-react-js/
These resources complement the techniques here and help you recognize patterns that cause Broken Access Control in WordPress.
Services That Pair Perfectly with These Fixes
Managed IT Services (for continuous security hygiene)
Proactive patching, backups, monitoring, and incident response that reduce the risk of Broken Access Control in WordPress coming back.
👉 pentesttesting.com/managed-it-services/
AI Application Cybersecurity (for AI-powered sites)
If your WordPress integrates AI endpoints or plugins, secure tokens, roles, and model-facing routes to stop privilege bypass.
👉 pentesttesting.com/ai-application-cybersecurity/
Offer Cybersecurity to Your Clients (for agencies)
White-label assessments and remediation plans you can deliver to clients—complete with Broken Access Control in WordPress checks.
👉 pentesttesting.com/offer-cybersecurity-service-to-your-client/
More Code Patterns You’ll Reuse
Deny Theme/Plugin Editors (reduce lateral movement)
// wp-config.php
define('DISALLOW_FILE_EDIT', true);Guard Shortcodes (often forgotten)
add_shortcode('private_note', function ($atts = []) {
if (!is_user_logged_in()) return '';
if (!current_user_can('read_private_notes')) return '';
$atts = shortcode_atts(['id' => 0], $atts);
$note = get_post((int)$atts['id']);
if (!$note) return '';
if ((int)$note->post_author !== get_current_user_id() &&
!current_user_can('read_post', $note->ID)) {
return '';
}
return wpautop(esc_html($note->post_content));
});Centralized Download Gate (replace direct links)
// Link: /download?f=reports/123.pdf
add_action('init', function () {
if (isset($_GET['f']) && strpos($_SERVER['REQUEST_URI'], '/download') === 0) {
$rel = sanitize_text_field(wp_unslash($_GET['f']));
$base = WP_CONTENT_DIR . '/uploads/private/';
$path = realpath($base . $rel);
if (!$path || !str_starts_with($path, $base)) {
status_header(404); exit;
}
if (!current_user_can('read_private_reports')) {
status_header(403); exit('Unauthorized');
}
header('Content-Type: application/pdf');
readfile($path);
exit;
}
});Final Word
Treat Broken Access Control in WordPress as a must-fix engineering item, not a nice-to-have. Build with least privilege, verify capabilities and ownership on every request, and gate your files behind server-side checks. When you’re ready for a deeper audit or remediation plan, our team can help—end-to-end.
Explore more on our blog: Pentest Testing Corp Blog
Try the free scanner: free.pentesttesting.com
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about Broken Access Control in WordPress.


Pingback: Best 7 Ways to Stop XSSI Attack in React.js