IDOR Vulnerability in WordPress: 7 Proven Ways to Fix It
If you manage a site or build plugins, you’ve probably heard of Broken Access Control—an OWASP Top 10 risk. A classic instance is the IDOR Vulnerability (Insecure Direct Object References) in WordPress. It happens when an attacker guesses or iterates an object identifier (post ID, order ID, file name, user ID) and the server returns that object without verifying ownership or permission.

This post explains how IDOR Vulnerability in WordPress appears in the real world, how to reproduce it safely, and seven proven, code-level remediations you can deploy today.
TL;DR checklist
- Validate ownership and permissions for every object access
- Prefer capabilities over roles; least privilege wins
- Use nonces to bind user intent, especially in state-changing requests
- Add
permissions_callbackto all custom REST routes - Never trust client-provided IDs—re-derive or look up securely server-side
- For downloads and media, verify ownership AND capability before streaming
- Log, test, and monitor suspicious ID patterns (sequences, UUID misuse)
What Is an IDOR Vulnerability in WordPress?
At its core, IDOR Vulnerability occurs when your code trusts a user-supplied identifier—like ?invoice_id=123 or ?user=42—without checking whether the current user is allowed to access that resource. In WordPress, this shows up in:
- Insecure AJAX handlers that return post meta for any
post_id. - Custom download endpoints that serve files by
?file_id=.... - Custom REST API routes missing a proper
permission_callback. - Admin pages that read
$_GET['user_id']and reveal another user’s data. - Widgets or shortcodes that expose predictable object IDs.
Because WordPress uses sequential post and user IDs, attackers can often enumerate identifiers—making IDOR Vulnerability especially risky if you don’t enforce object-level authorization.
A Quick Demo: Insecure vs Secure (AJAX Example)
❌ Insecure AJAX Handler (Vulnerable to IDOR)
// functions.php (or your plugin main file)
add_action('wp_ajax_get_invoice', 'acme_get_invoice');
add_action('wp_ajax_nopriv_get_invoice', 'acme_get_invoice'); // mistake: exposing to unauth users
function acme_get_invoice() {
$invoice_id = intval($_GET['invoice_id'] ?? 0);
global $wpdb;
// Returns invoice row by ID but never checks ownership or capabilities
$invoice = $wpdb->get_row(
$wpdb->prepare("SELECT * FROM {$wpdb->prefix}invoices WHERE id = %d", $invoice_id)
);
// ❌ IDOR Vulnerability in WordPress: any logged-out user can pull any invoice by ID
wp_send_json_success($invoice);
}✅ Secure AJAX Handler (Ownership + Capability + Nonce)
add_action('wp_ajax_get_invoice', 'acme_get_invoice_secure');
function acme_get_invoice_secure() {
// Require authentication
if (!is_user_logged_in()) {
wp_send_json_error(['message' => 'Auth required'], 401);
}
// Verify nonce to prevent CSRF + ensure intent
if (!isset($_POST['_wpnonce']) || !wp_verify_nonce($_POST['_wpnonce'], 'acme_get_invoice')) {
wp_send_json_error(['message' => 'Invalid nonce'], 403);
}
$current_user_id = get_current_user_id();
$invoice_id = intval($_POST['invoice_id'] ?? 0);
// Capability check: only customers or admins can view invoices
if (!current_user_can('read') && !current_user_can('manage_options')) {
wp_send_json_error(['message' => 'Insufficient permissions'], 403);
}
global $wpdb;
$invoice = $wpdb->get_row(
$wpdb->prepare(
"SELECT * FROM {$wpdb->prefix}invoices WHERE id = %d AND user_id = %d",
$invoice_id,
$current_user_id
)
);
if (!$invoice && !current_user_can('manage_options')) {
wp_send_json_error(['message' => 'Not found'], 404);
}
wp_send_json_success($invoice);
}Image of our Website Vulnerability Scanner homepage:

How to Test for IDOR the Right Way
To validate whether IDOR Vulnerability in WordPress exists, try these safe steps on a staging site:
- Switch Accounts: Create two normal users (User A and User B). While authenticated as User A, capture requests (AJAX or REST) that fetch resources by ID.
- Replay IDs: Replace User A’s
post_id/invoice_idwith an ID belonging to User B. If your server returns B’s data to A, you have an IDOR Backdoor. - REST API Checks: For custom routes, confirm
permission_callbackrestricts access by capability and resource ownership. - File Download Paths: Ensure direct file URLs or predictable
?file_id=parameters don’t serve other users’ files. - Use a Scanner: Run our Free Website Security Scanner to catch common misconfigurations and get a baseline report you can share with your team.
7 Proven Ways to Fix IDOR Vulnerability in WordPress
These patterns directly reduce the risk of IDOR Vulnerability. Sprinkle them across AJAX, REST, templates, and admin pages to harden WordPress security without hurting UX.
1) Lock Down REST Routes with permission_callback
add_action('rest_api_init', function () {
register_rest_route('acme/v1', '/profile/(?P<user_id>\d+)', [
'methods' => 'GET',
'callback' => 'acme_get_profile',
'permission_callback' => function (WP_REST_Request $request) {
$target_user = intval($request['user_id']);
$current = get_current_user_id();
if (!$current) return false;
// Allow self-access or admins
return ($current === $target_user) || current_user_can('list_users');
}
]);
});
function acme_get_profile(WP_REST_Request $request) {
$user_id = intval($request['user_id']);
$user = get_userdata($user_id);
if (!$user) {
return new WP_Error('not_found', 'User not found', ['status' => 404]);
}
// Only return safe fields
return [
'id' => $user->ID,
'email' => ($user->ID === get_current_user_id() || current_user_can('list_users')) ? $user->user_email : null,
'name' => $user->display_name,
];
}This pattern prevents IDOR Vulnerability in WordPress by enforcing object-level authorization on the server.
2) Require Nonces for State-Altering and Sensitive Reads
// Enqueue nonce in your script localized data
wp_enqueue_script('acme', plugin_dir_url(__FILE__).'assets/app.js', ['jquery'], '1.0', true);
wp_localize_script('acme', 'acmeData', [
'ajaxUrl' => admin_url('admin-ajax.php'),
'nonce' => wp_create_nonce('acme_sensitive_read'),
]);
// Server side
add_action('wp_ajax_acme_sensitive_read', function() {
check_ajax_referer('acme_sensitive_read');
// ...proceed with tight capability and ownership checks...
});Nonces don’t replace authorization, but they complement it to reduce CSRF-driven IDOR chains.
3) Use Indirect References (Opaque Tokens), Not Raw IDs
Instead of exposing ?file_id=1001, use a short-lived, signed token that maps to the file and the owning user.
function acme_sign_token($data, $ttl = 600) {
$payload = array_merge($data, ['exp' => time() + $ttl]);
$json = wp_json_encode($payload);
$sig = hash_hmac('sha256', $json, AUTH_SALT);
return base64_encode($json.'.'.$sig);
}
function acme_verify_token($token) {
$decoded = base64_decode($token, true);
if (!$decoded || !str_contains($decoded, '.')) return false;
list($json, $sig) = explode('.', $decoded, 2);
if (!hash_equals(hash_hmac('sha256', $json, AUTH_SALT), $sig)) return false;
$data = json_decode($json, true);
if (!$data || time() > ($data['exp'] ?? 0)) return false;
return $data;
}4) Enforce Ownership in Queries (No “Naked” IDs)
$current = get_current_user_id();
$query = new WP_Query([
'post_type' => 'invoice',
'posts_per_page' => 1,
'p' => intval($_GET['invoice_id'] ?? 0),
'author' => $current, // ownership enforcement!
]);
if ($query->have_posts()) {
// OK to show
} else {
// Not found or not yours
}This stops post enumeration—one of the leading paths to IDOR Vulnerability in WordPress.
5) Secure File Downloads (Never Trust the Path)
add_action('init', function () {
add_rewrite_rule('^download/([a-zA-Z0-9_-]+)/?', 'index.php?acme_token=$matches[1]', 'top');
});
add_filter('query_vars', function ($vars) { $vars[] = 'acme_token'; return $vars; });
add_action('template_redirect', function () {
$token = get_query_var('acme_token');
if (!$token) return;
$data = acme_verify_token($token);
if (!$data) wp_die('Invalid token', 403);
// Ensure the current user matches the owner in token
if (get_current_user_id() !== intval($data['user_id']) && !current_user_can('manage_options')) {
wp_die('Forbidden', 403);
}
// Map file ID to a safe, non-web-accessible path
$file_path = get_user_meta($data['user_id'], 'acme_file_'.$data['file_id'], true);
if (!$file_path || !file_exists($file_path)) wp_die('Not found', 404);
// Stream the file with proper headers
header('Content-Type: application/octet-stream');
header('Content-Disposition: attachment; filename="'.basename($file_path).'"');
readfile($file_path);
exit;
});This pattern minimizes IDOR Vulnerability for downloads by validating ownership and using a signed token.
6) Capabilities Over Roles, and the Principle of Least Privilege
// Example: add a fine-grained capability used only for viewing invoices.
function acme_add_caps() {
$role = get_role('shop_manager');
if ($role && !$role->has_cap('view_own_invoices')) {
$role->add_cap('view_own_invoices');
}
}
register_activation_hook(__FILE__, 'acme_add_caps');Check current_user_can('view_own_invoices') instead of assuming role names.
7) Monitor & Log Access Attempts
function acme_log_access($resource, $resource_id, $allowed) {
error_log(sprintf(
'[ACME] %s access to %s:%d by user:%d ip:%s',
$allowed ? 'ALLOWED' : 'DENIED',
$resource,
$resource_id,
get_current_user_id(),
$_SERVER['REMOTE_ADDR'] ?? 'cli'
));
}Logs give you a paper trail when you suspect IDOR Vulnerability in WordPress exploitation.
More Secure Patterns (Copy-Paste Ready)
Validate Ownership with a Helper
function acme_user_owns_post($post_id, $user_id = null) {
$user_id = $user_id ?: get_current_user_id();
$post = get_post($post_id);
if (!$post) return false;
return intval($post->post_author) === intval($user_id);
}Combine Ownership + Capability Checks
function acme_can_view_invoice($invoice_id, $user_id = null) {
$user_id = $user_id ?: get_current_user_id();
if (current_user_can('manage_options')) return true;
global $wpdb;
$owner = (int) $wpdb->get_var(
$wpdb->prepare("SELECT user_id FROM {$wpdb->prefix}invoices WHERE id = %d", $invoice_id)
);
return $owner === (int) $user_id;
}Always Prepare DB Statements
global $wpdb;
$invoice_id = intval($_GET['invoice_id'] ?? 0);
$row = $wpdb->get_row(
$wpdb->prepare("SELECT * FROM {$wpdb->prefix}invoices WHERE id = %d AND user_id = %d", $invoice_id, get_current_user_id())
);Harden Admin Screens Reading $_GET
if (!current_user_can('edit_posts')) {
wp_die('Forbidden', 403);
}
$target_user = intval($_GET['user_id'] ?? 0);
if ($target_user && $target_user !== get_current_user_id() && !current_user_can('list_users')) {
wp_die('Forbidden', 403);
}Each of these patterns reduces the window for IDOR Vulnerability while improving overall WordPress security.
Real-World Checklist to Avoid IDOR
- Never rely on client-provided IDs without verifying ownership on the server.
- For REST API, always define
permission_callback. - For AJAX, require login (
is_user_logged_in()), verify nonces, and check capabilities. - Hide internal IDs where possible; prefer short-lived, signed, opaque tokens.
- Ensure files live outside web root and are served by controlled handlers.
- Log denied attempts to spot enumeration.
- Regularly run a vulnerability scanner and perform manual access control tests.
Want a quick baseline? Run our Free Website Security Scanner and then harden any endpoints flagged during your assessment.
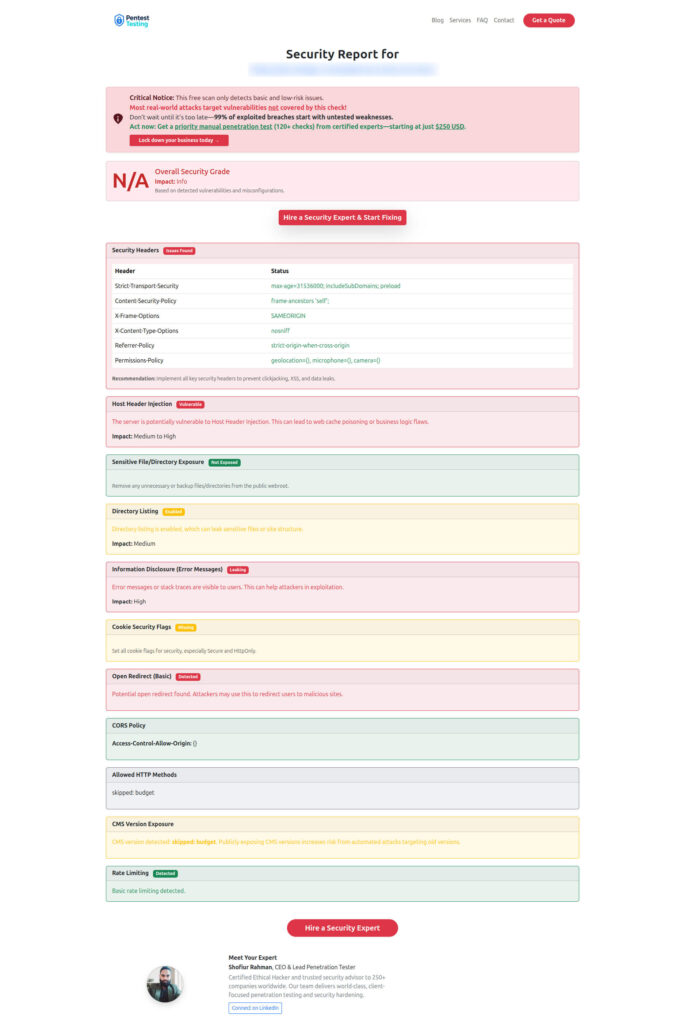
Sample Assessment Report from our tool to check Website Vulnerability:
Related Reading & Internal Links
- Explore our WordPress security guides, including CSRF prevention in WordPress and practical hardening tips.
- See our research note on TR-069 exposure in Italian business networks—a reminder that weak access controls show up beyond WordPress.
- If you run an eCommerce stack, read Prevent SQL Injection in OpenCart to round out your application security posture.
- If login abuse or session hijacks are on your radar, don’t miss our step-by-step guide: Broken Authentication in WordPress. Copy-paste PHP/NGINX snippets included.
- For front-end auth pitfalls, here’s a complementary read from our other site: JWT Attacks in React.js—great for anyone managing SPAs that integrate with WordPress APIs.
- Browse more posts on our Pentest Testing Blog.
These resources complement everything we covered about IDOR Vulnerability and broader WordPress security.
Our Services (Tailored to Your Stack)
Managed IT Services
Harden endpoints, segment networks, monitor logs, and respond fast. Learn more: Managed IT Services.
- Patch management and uptime monitoring
- Endpoint hardening and zero-trust basics
- Rapid incident triage aligned to your CMS stack
AI Application Cybersecurity
If your WordPress site integrates LLMs or AI features, secure prompts, webhooks, and plugins from the ground up: AI Application Cybersecurity.
- Model-in-the-loop threat modeling
- Prompt injection and data exfiltration defenses
- Secure AI plugin design reviews
Offer Cybersecurity Service to Your Client (Partner Program)
Agencies, MSPs, and studios: bundle security into your offerings with white-label penetration testing and monitoring. Details here: Offer Cybersecurity Service to Your Client.
- White-label reports and dashboards
- Margin-friendly pricing, smooth delivery
- Direct access to our senior testers
These services help teams eliminate IDOR vulnerabilities and raise overall WordPress security maturity.
Conclusion
IDOR Vulnerability in WordPress is common because object IDs are predictable, and developers are busy. The cure is consistent server-side authorization: tight permission_callback in REST, nonces + capability checks in AJAX, ownership enforcement in queries, and indirect references for sensitive objects. Apply the seven patterns above, run a vulnerability scan, and keep iterating. Your users—and your audit logs—will thank you.
🔐 Frequently Asked Questions (FAQs)
Find answers to commonly asked questions about IDOR Vulnerability in WordPress.

